Zellic Security Roundup: April '25
Volume 2, Issue 4
Welcome to the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month we will dive into our recent blog post, which discusses the Bitcoin scripting system and how several projects use Bitcoin’s features, as well as cover recent Zellic audit reports and security-focused news in Web3.
Zellic Research & Writing
Below is a snippet from our blog post “Building with Bitcoin: A Survey of the Use of Its Scripting System Across Projects” written by Zellic Security Researcher Avi Weinstock.
We’ll be looking at how BitVM and BitVM2 are building on Bitcoin.
If you’d like to familiarize yourself with some of the key elements of Bitcoin’s system, including
BIP-340 Schnorr signatures,
Script VM,
pay-to-pubkey hash,
pay-to-script hash,
SegWit version 0,
Taproot scripts,
Covenants and Covenant Emulation Committees, and
FROST signatures,
check out our full blog post here.
BitVM
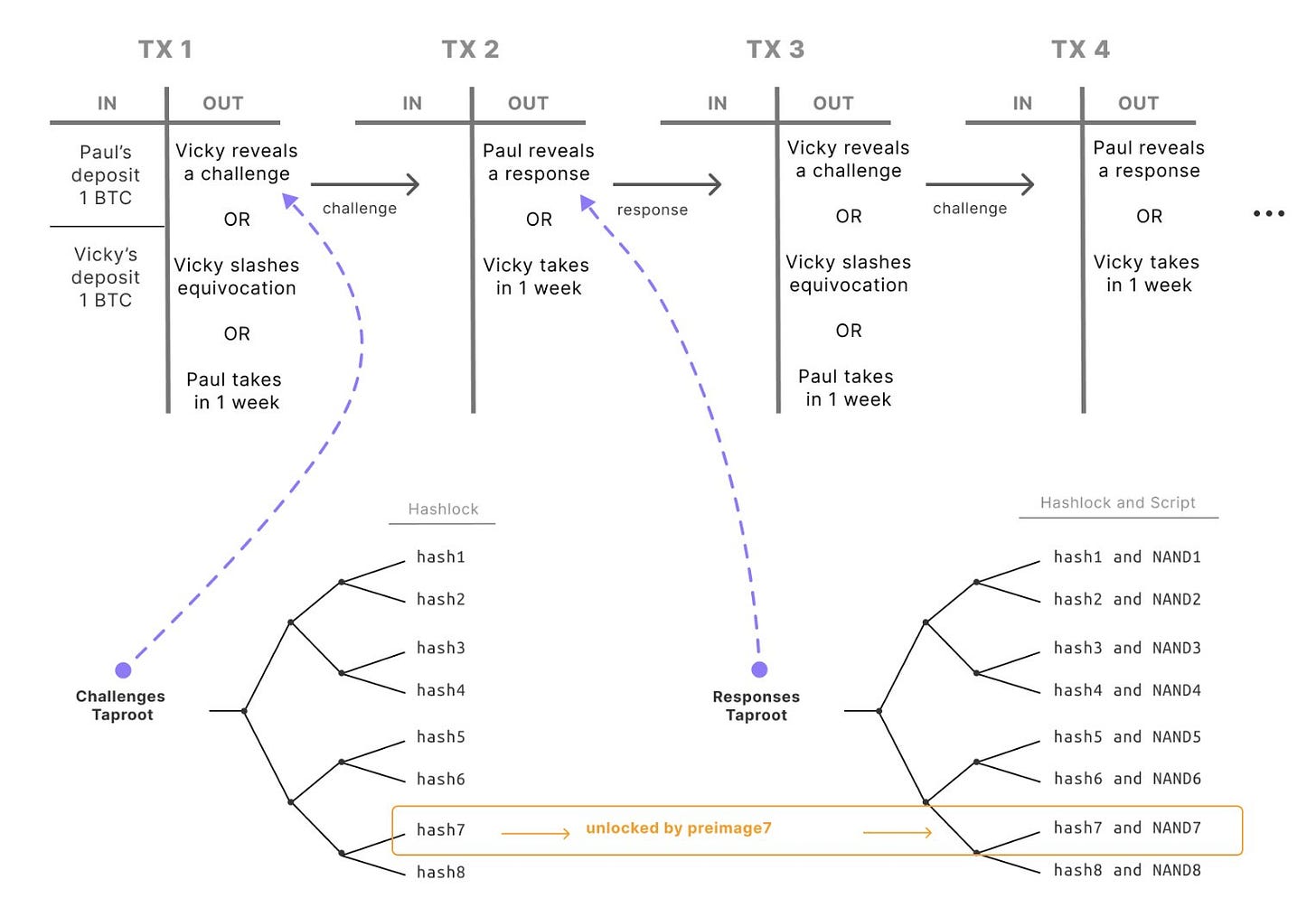
BitVM allows a prover and a verifier to commit to a circuit using Taproot scripts.
The UTXO can be spent based on the circuit's outcome: if the prover correctly evaluates the circuit, they claim it; if they fail or cheat, the verifier does.
Direct execution in Bitcoin script is inefficient for large circuits, so BitVM optimizes this. In the optimistic scenario, if there's a dispute, an interactive fraud proof is used, taking time proportional to the circuit's depth.
To prove that BitVM works for any computation, boolean circuits are compiled using bit commitments and NAND gates, though arithmetic circuits can also be used in implementations for efficiency.
Each bit in the circuit has preimages (`w_0`, `w_1`) stored in a Taproot script that allows the verifier to claim the deposits if the prover reveals both. Each NAND gate is encoded as a script that verifies logical operations on chain if necessary.
If a dispute arises, the verifier requests evaluations for specific gates using hashlocked challenges.
The prover and verifier take turns advancing the state machine via presigned transactions. If the prover contradicts their prior commitments, the verifier can prove fraud and claim the deposit.
The fraud proof begins with the verifier challenging the final output gate. If disagreement exists, they work backward through the circuit, round by round, until they find an input inconsistency. If the verifier proves an inconsistency, they win the deposit. Otherwise, if no contradiction appears after the required steps, the prover’s evaluation is accepted.
BitVM does not preserve input privacy. The prover's inputs are fully visible both on chain and to the verifier. If the verifier's inputs were hidden from the prover, the prover would not be able to evaluate the circuit for the fraud proof. However, BitVM can verify inner zero-knowledge proofs, as demonstrated by BitVM Bridge.
BitVM2
BitVM2 builds on BitVM by improving efficiency and flexibility.
Instead of committing to a boolean circuit, the prover commits to a Bitcoin script of arbitrary length, split into chunks that fit within Bitcoin’s script size limits. This change allows fraud proofs to be resolved in a constant number of rounds, rather than a logarithmic number based on the circuit’s size.
This is because the evidence of fraud is a chunk for which the prover signs input and output stacks that are inconsistent with the chunk's execution, instead of a log-sized path through the circuit terminating on an inconsistent input bit.
Additionally, unlike BitVM, BitVM2 allows any Bitcoin user to act as a verifier, eliminating the need for a preestablished prover-verifier setup.
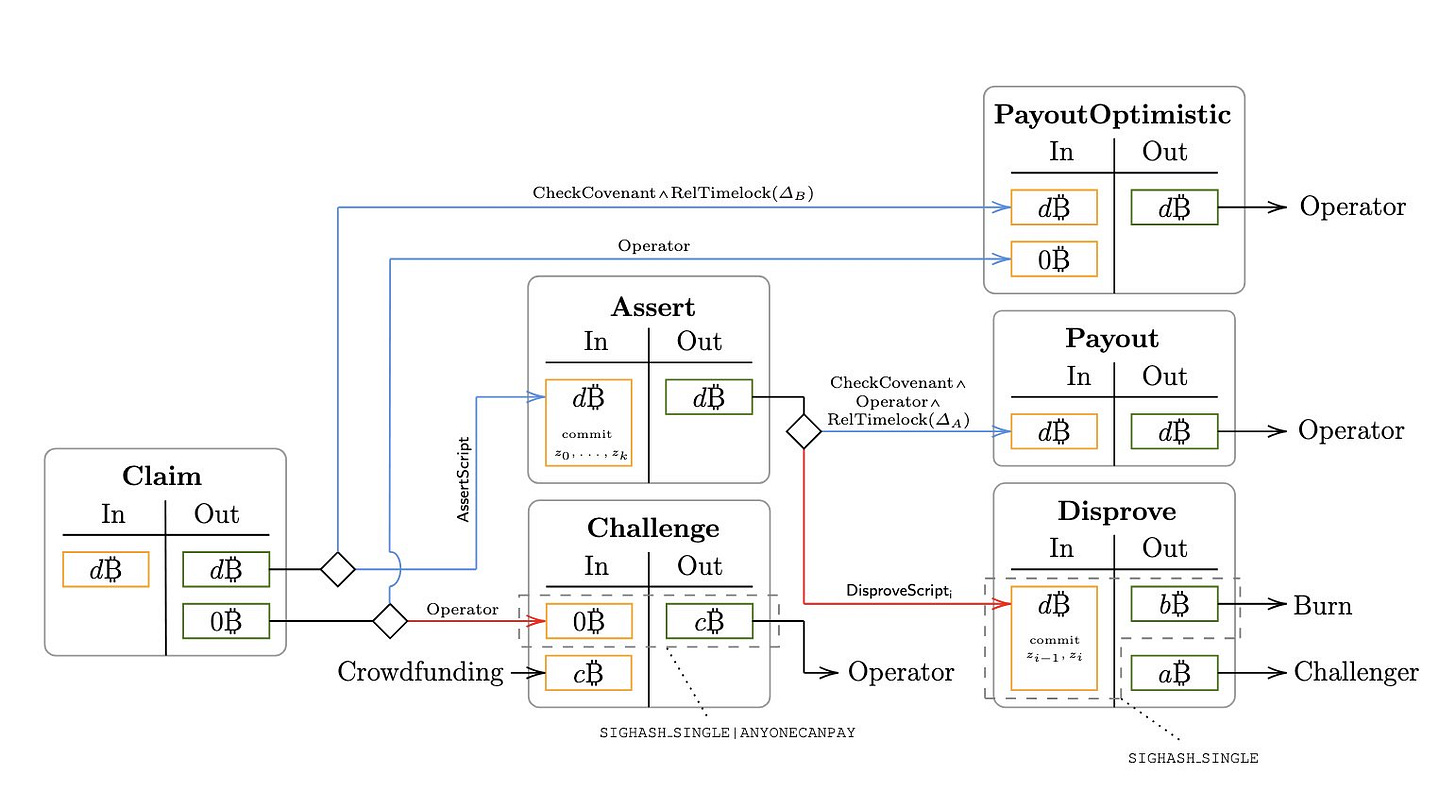
To execute a program, the prover sets up a series of six linked transactions.
`Claim`, which initializes execution with a funding input and specifies the initial stack value, creates a Taproot output with a timelock path for optimistic payout and an `Assert` path to commit intermediate states, and includes a zero-value connector output to prevent conflicts between later transactions.
`PayoutOptimistic`, which allows the prover to claim their deposit via the timelock path if no challenge is issued, avoiding unnecessary on-chain commitments.
`Challenge`, which enables a verifier to dispute the execution by submitting a challenge and requires the verifier to pay a fee, discouraging spam challenges and covering the prover’s cost of publishing the `Assert` transaction.
`Assert`, which commits intermediate stack values and Lamport keys on chain, allows challenges for each program chunk, and includes a success path for the prover to claim their deposit after a timelock.
`Disprove`, which is used when fraud is detected, proving incorrect execution of a chunk; burns part of the deposit; and transfers the remainder to the verifier.
`Payout`, which, if no fraud is found, executes the timelock path, allowing the prover to withdraw their deposit.
Unlike BitVM, which relies on step-by-step fraud proofs working backward from the final output on chain, BitVM2 enables an off-chain verifier to check execution forward chunk by chunk.
The prover signs the stack state after executing each chunk, allowing an off-chain verifier to detect mismatches between inputs and outputs. If a discrepancy is found, the verifier can present an on-chain proof showing an invalid transition.
Lamport signatures in BitVM2 are used as a signature scheme, verifiable within Bitcoin script, to work around Bitcoin lacking `OP_CHECKSIGFROMSTACK`. Note that for 1-bit Lamport signatures, the keys are equal to the signatures.
BitVM2 powers BitVM Bridge, enabling BTC transfers between Bitcoin and other blockchains. The bridge requires the counterparty blockchain to maintain a Bitcoin light client and post its state to Bitcoin. Users send BTC by submitting a Bitcoin transaction that the counterparty recognizes, minting bridged BTC on the other chain.
Users on the counterparty blockchain can send BTC back to Bitcoin by burning the bridged BTC and producing a Groth16 proof that the bridged BTC was burned, which is verified by BitVM2 instances on Bitcoin.
In the News
Hacks
A trader swapped ~$733K of USDC for just ~$19K in USDT potentially as a result of a sandwich attack.
Conic Finance, a DeFi protocol that once held more than $156M, has shut down more than a year after a pair of exploits that totaled $3.3M in exploited funds.
The ESP32 microchip, made by Espressif and used by over one billion units as of 2023, has been found to contain undocumented commands that allow “spoofing of trusted devices, unauthorized data access, pivoting to other devices on the network, and potentially establishing long-term persistence”.
Abracadabra Finance, a decentralized lending platform, suffered an exploit of $13M worth of cryptocurrency from pools linked to GMX liquidity tokens.
Zoth, a RWA restaking protocol, suffered an exploit that led to over $8.4M in losses, marking the second security breach for Zoth within a month. The stolen funds have been converted into 4,223 ETH.
Bybit CEO Ben Zhou disclosed that the hackers responsible for the $1.5B hack have exchanged 86% of the stolen funds for 12,836 BTC, which were distributed across 9,117 wallets (averaging to 1.41 BTC per wallet).
Polymarket suffered a governance attack where an individual used its voting power to manipulate the oracle, which allowed the market to settle false results, leading to a successful profit.
The JELLY token was delisted by Hyperliquid following suspicious trading activity; this post is a timeline of how that short squeeze occurred on March 26th.
Research
The Chopping Block podcast recently discussed the bugs that Zellic discovered in elizaOS, during a recent conversation on the potential security concerns with AI.
Check out the full thread on the two old-school bugs that we found while looking into elizaOS here.
North Korea has established Research Center 227 with a focus on developing, amongst other initiatives, AI-based information-theft technologies and establishing automated programs for information collection/analysis.
Unit42 published research on a GitHub Actions supply-chain attack following an in-depth investigation into how attackers compromised CI/CD pipelines of thousands of repositories, putting them at risk. Unit42 discovered that the initial attack targeted Coinbase; however, the attacker was not able to use Coinbase secrets or publish packages.
According to DeFiLlama, real-world assets are now a $10B category, with Maker, BUIDL by BlackRock, and USDtb by Ethena each accounting for more than $1B in TVL.
“The Lessons of Crypto Media” is a look into the history of crypto media through the lens of various crypto events including the early years of Bitcoin, FTX crash, Trump’s presidency, and more.
The Security Alliance (SEAL) has released four advisory posts on DPRK’s threat to crypto exchanges, reflected XSS exploits by Perpetual Drainer, ELUSIVE COMET, and SLOVELNY COMET.
“Demystifying the North Korean Threat” is an article by samczsun that goes into how the DPRK operates, including tactics and procedures.
Legal
United States Treasury officials have lifted sanctions on Tornado Cash in the Treasury’s latest filing in Van Loon v. Department of the Treasury.
Infini, a stablecoin-payment platform, has filed a lawsuit against a developer and three unidentified persons with access to wallets involved in the $49M hack that took place in late February.
Crime
The operator of Garantex, a defunct illicit crypto exchange, was arrested in India after being accused of facilitating the laundering of illicitly obtained cryptocurrency.
Rostislav Panev was arrested and extradited to the United States for his role as a developer of the LockBit ransomware group. The LockBit group has attacked more than 2,500 victims, including 1,800 individuals in the United States.
Scams
The Department of Financial Protection and Innovation (DFPI) released a crypto scam tracker based on consumer complaints, which “represent descriptions of losses incurred in transactions that complainants have identified as part of a fraudulent or deceptive operation”.
The Illinois State Senate has passed the Digital Assets and Consumer Protection Act, which aims to address the mounting problem of crypto fraud. Illinois residents experienced over $163M in crypto fraud losses in 2023 alone.
A wallet linked to the ZKasino scammer has lost more than $27M after a leveraged position was liquidated.
Meet Up With Us
We won’t be traveling in April, but if you’d like to set up 1:1 time with our team, then reach out to sales@zellic.io for scheduling!
Zellic Auditing Stats
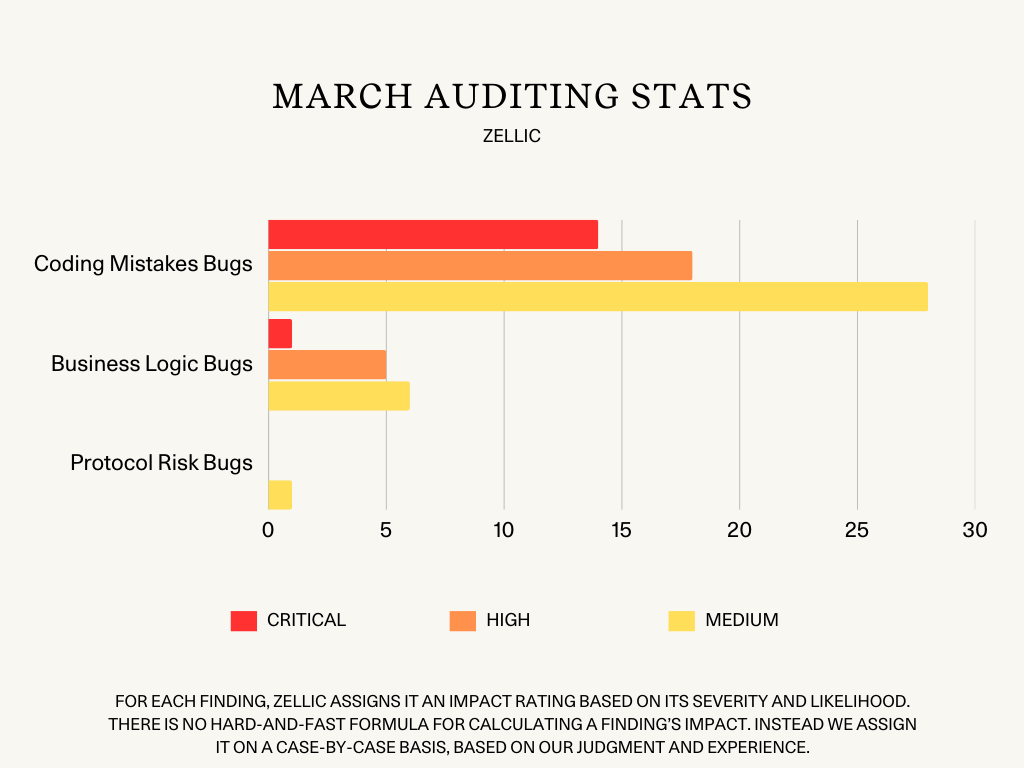
In March, Zellic auditors completed 37 audit engagements where they were able to uncover a total of 73 Critical, High, and Medium bugs:
15 Critical-level bugs
14 Coding Mistakes bugs
1 Business Logic bug
23 High-level bugs
18 Coding Mistakes bugs
5 Business Logic bugs
35 Medium-level bugs
28 Coding Mistakes bugs
6 Business Logic bugs
1 Protocol Risk bug
Recent Zellic Audit Reports
Cultured Audit Report: Cultured is a framework that allows users to trade on arbitrary data feeds.
Circuit DAO Audit Report: Circuit is a CDP protocol built on Chia.
AtomOne Audit Report: AtomOne is a community-driven fork of the Cosmos Hub.
Rujira Audit Report: Rujira is the app layer for THORChain.
About Us
Zellic specializes in securing emerging technologies. Our security researchers have uncovered vulnerabilities in the most valuable targets, from Fortune 500s to DeFi giants.
Developers, founders, and investors trust our security assessments to ship quickly, confidently, and without critical vulnerabilities. With our background in real-world offensive security research, we find what others miss.
Contact us for real audits, not rubber stamps.