Zellic Security Roundup: September '24
Volume 1, Issue 8
Welcome to the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month will focus on Zellic’s acquisition of Code4rena and the latest news in Web3 security.
Cool Finds at Zellic
Below is a snippet from our blog post “Why We Acquired Code4rena”.
From Audits to Audits+
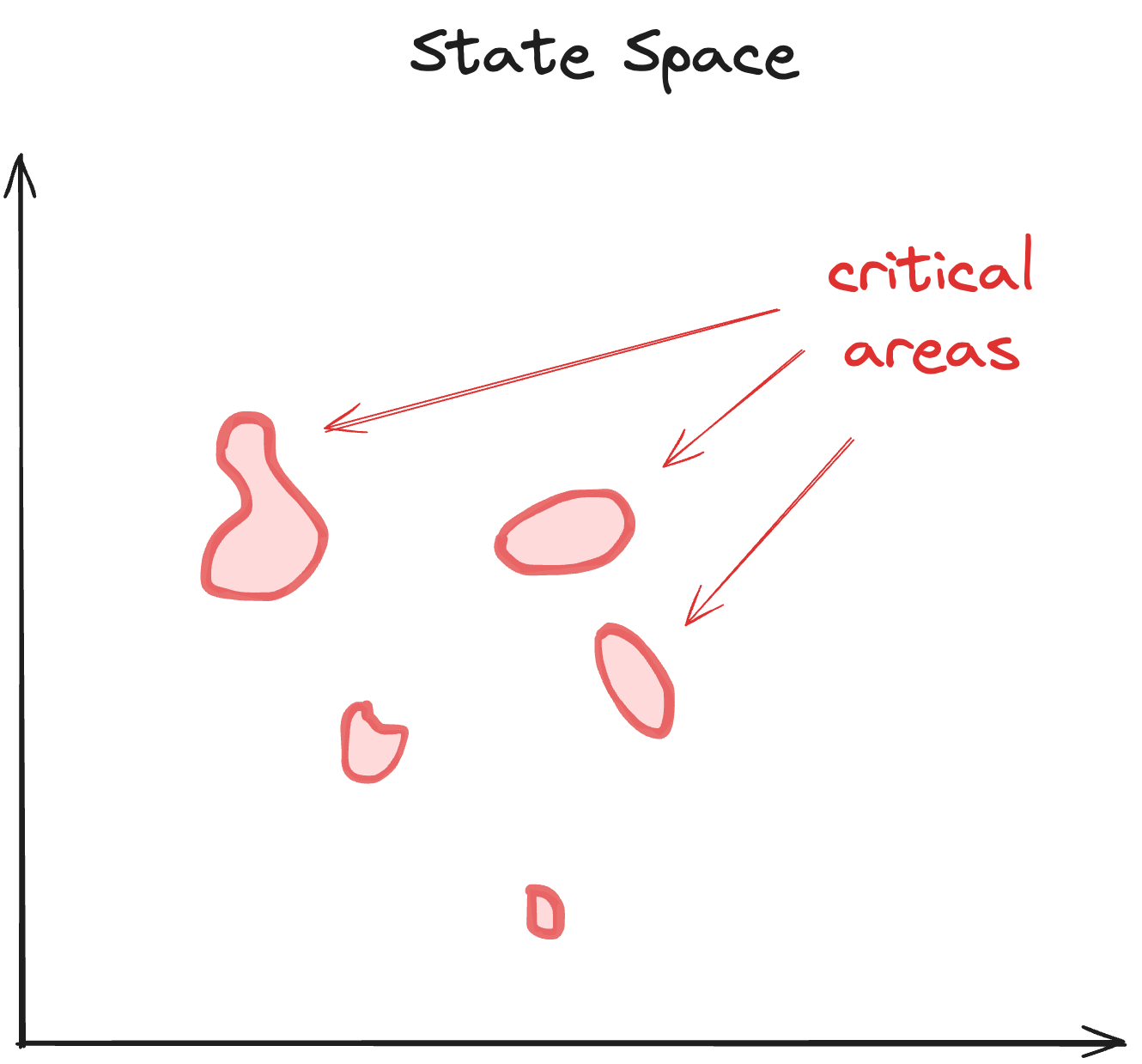
Let’s talk about code in general. For any piece of software, there are a few critical security properties that absolutely must hold. For a bridge or a DeFi app, this would be that funds can’t be stolen or that funds can’t be bricked. For a Cosmos chain, this would be that the chain doesn’t halt. For a perps DEX, this would be that users can’t get infinite leverage or intentionally create bad debt. For a wallet, this would be that we’re not logging users’ seed phrases to disk or the cloud. Here is a visual aid:
Now, Zellic’s audits are consultative and time-boxed. We are trying to break your code in catastrophic ways. We’re thinking, How can I steal all the funds? Does your mechanism actually work? What about this or that loophole? We focus on these things because our #1 priority is you not getting hacked. But since our audits are time-boxed, we naturally have less time to enumerate every single possible avenue. We have to allocate our time judiciously and seriously cover a few essential, critical components and attack vectors. Unfortunately, this means we sometimes have to deprioritize low and informational findings over noncritical parts of the codebase.
While we staff our audits with world-renowned researchers and CTF winners, this trade-off has been a consistent pain point for us. We don’t want to have to choose between focusing on the crits or catching every possible issue. Why can’t we have both? After all, our customers deserve that. Whenever we miss anything—even if it’s a low-severity finding—we feel just as bad as you do.
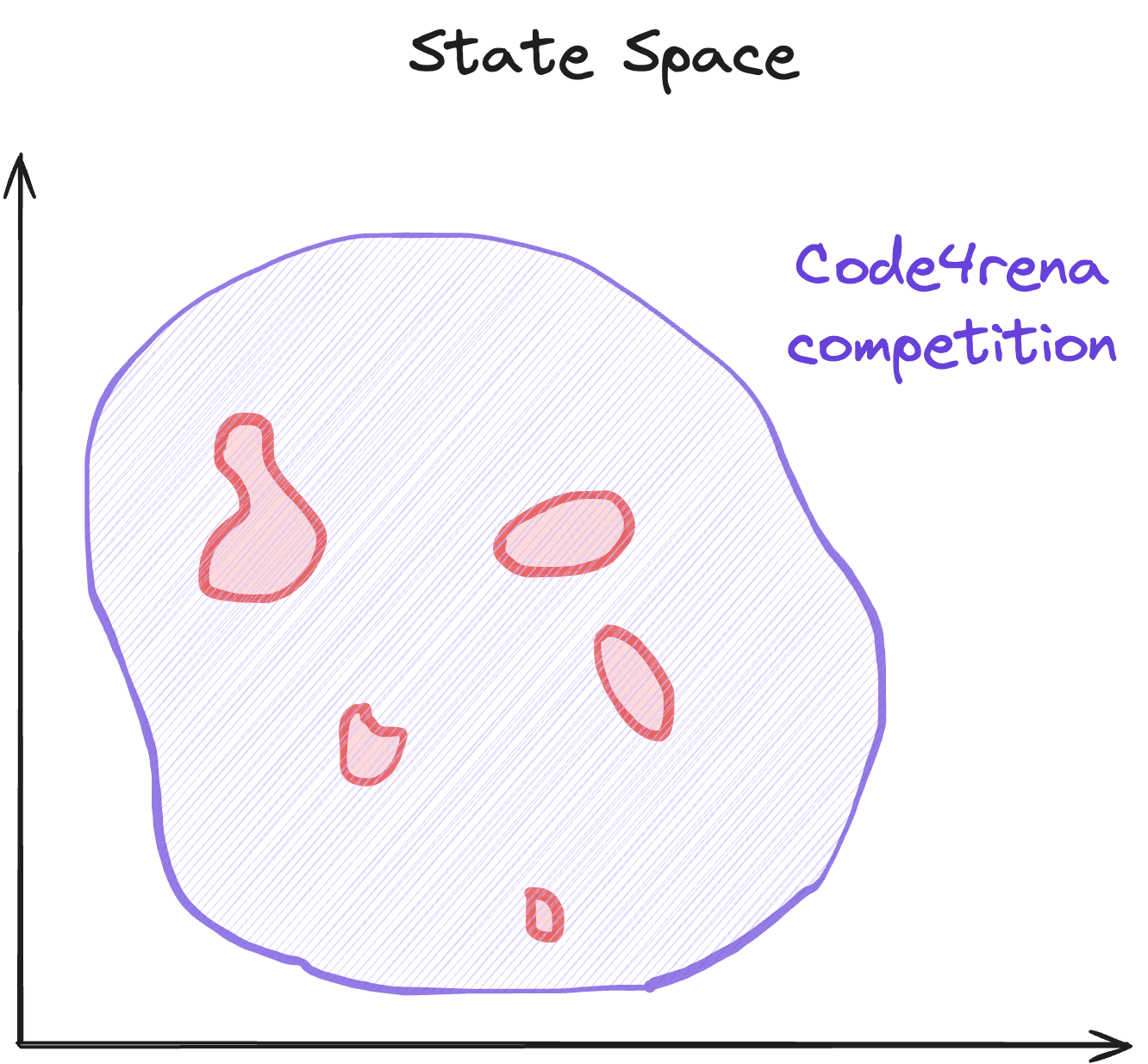
That’s where Code4rena comes in. Unlike consultative audits, competitive audits are bound by the prize pool size. Rather than a handful of gigachads, you get an entire community of Wardens (independent auditors) who will pick your code apart until it’s clean to the bone. Regardless of the nature of the issue, they will look for and report it. And that’s not to say that a Code4rena competition isn’t going to catch deep bugs. They do, and “dark horses”—previously unknown auditors who demonstrate immense depth and thoroughness—regularly appear in competitions↗, outperforming even well-established auditors.
Finally, by pairing a Zellic audit with a Code4rena competition, you get a new hybrid engagement that outclasses any individual audit. First, Zellic comes in to ensure that the priorities are taken care of. Then, a Code4rena competition brings a wide range of coverage for all kinds of potential issues, including not just the critical components but also things like integration and auxiliary contracts. There are no more trade-offs: clients get the concentrated assurance of a Zellic audit but with the as-many-eyes-on-the-code-as-possible benefits of a competitive audit.
Consultative audits and competitive audits are complementary. They’re not replacements or substitutes. The best security comes from getting both.
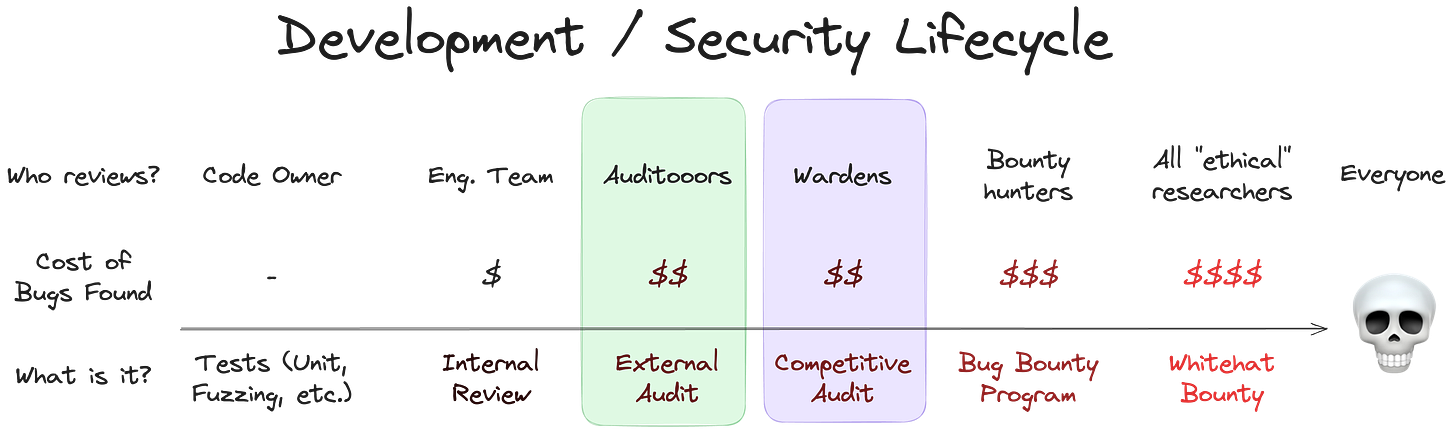
Here’s another way to look at it. Here’s what most software development looks like and how expensive it is to catch bugs at each stage of development.
As you go from earlier to later stages of development, the code is under scrutiny from more and more people. Beginning with just a single code owner, the person originally writing the code, you eventually reach every potential adversary in the world. And of course, the earlier you catch a bug, the cheaper it is. Before, Zellic sat squarely near the middle:
For security-minded projects, the most natural next step after us is a competitive audit. In fact, we were already proactively recommending our clients to do this:
But if you think about it, there’s a lot of inefficiency here. Administering a competitive audit is a lot of work. You have to decide what scope you want to be reviewed; then you need to provide the Wardens with guidance on what attack vectors to look for; and finally, you have to help judges evaluate all of the findings, which is tremendously laborious. That’s all on top of the ordinary logistical work of sales calls, vendor selection, legal document redlining and signing, invoicing and collecting accounts receivables, KYB… and on and on. And you have to do this twice for both the consultative audit and the competitive audit.
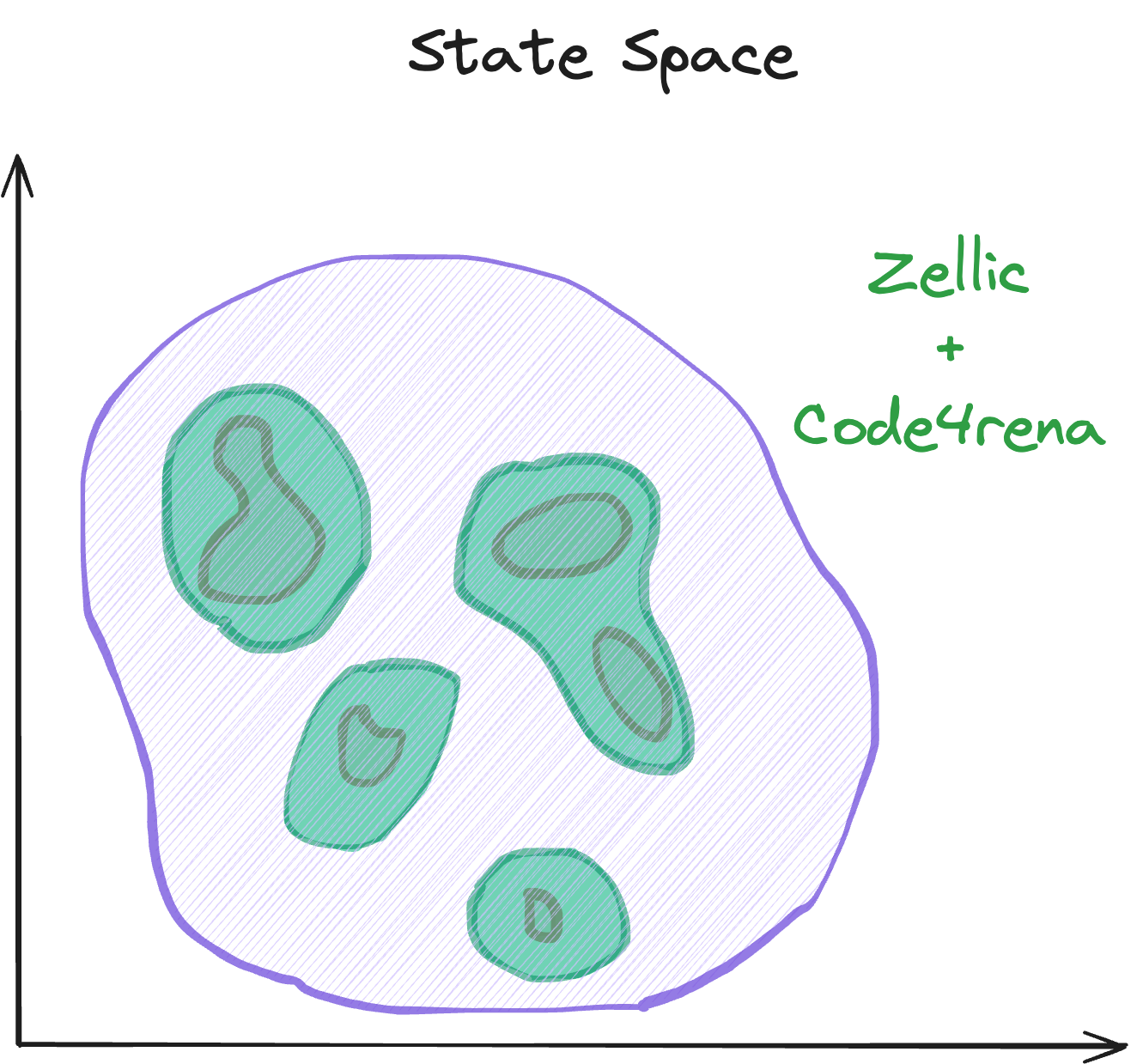
So the obvious solution here is to combine both these steps into a single, cohesive service, which we call Audits+:
Not only is this more efficient, it gets clients BETTER SECURITY with LESS HASSLE. That’s because our auditors—who have already spent days or weeks reviewing the project—know where the most important scope is and what attack vectors to pay attention to. They can guide the Wardens, answer questions, and help review findings, with minimal involvement from the client (who of course is kept in the loop with full visibility the whole time).
In Zellic audits, we always include a detailed threat model exercise, and we document the results in the audit report. These threat models are extremely thorough and outline exactly how the protocol works and what can go wrong. Being able to finish a consultative audit and hand that prep work to a hundred auditors is pretty incredible. When starting a time-boxed audit, you have no idea what you’re in for, particularly where you might wish for more time. In this combination, instead of a consultative audit being constrained, a strategic handoff turns the auditor’s work into a force multiplier through the competitive audit.
In short: Zellic audits combined with Code4rena competitions is a killer combination that gets our clients better security, more quickly, and more affordably.
Zellic Research & Writing
Why We Acquired Code4rena
How Zellic's acquisition of Code4rena benefits you.
Two Vulnerabilities in gnark's Groth16 Proofs
An analysis of two vulnerabilities Zellic discovered that broke zero-knowledge and soundness of gnark’s Groth16 proofs with commitments.
In the News
Zellic’s Acquisition of Code4rena
Zellic’s thread officially announcing the acquisition of Code4rena
The Block — Zellic acquires Paradigm-backed smart contract audit platform C4
The cofounder of C4, Sock, posts a thread on the announcement that C4 is joining Zellic
Code4rena’s thread announcing Zellic’s acquisition of Code4rena
Research
“Calling All Hackers” is an article written by Zellic CEO Luna Tong and featured in the latest edition of Phrack Magazine.
Microsoft released a patch to fix 90 security vulnerabilities in Windows including six zero-day vulnerabilities that attackers were exploiting at the time.
Hacks
Ronin Network was exploited for ~$12M in ETH and USDC (the maximum amount of ETH/USDC that could be withdrawn from the bridge for one single transaction) by a group of white-hat hackers. The funds were returned following the exploit.
TRM Labs, a blockchain investigations and risk management firm, showed a surge in crypto hacks and exploits in the first half of 2024. TRM’s threat intelligence team states that by June 24, 2024, hackers stole $1.38B compared to $657M this time last year.
According to a recent Immunefi report, “the crypto industry saw a total of $1.21 billion worth of digital assets lost to hacks and rug pulls year-to-date (YTD) in 2024 across 154 individual exploits”.
The McDonald’s Instagram account was taken over by hackers who used the account to promote a fake Grimace Coin to scam users for $700,000.
The hackers that stole almost 2.7B records of personal information for people in the US have leaked the information on a forum exposing names, social security numbers, physical addresses, and possible aliases.
Crime
The US has traded Russian cybercriminals in exchange for Wall Street Journal reporter Evan Gershkovich and ex–US Marine Paul Whelan.
The domain of the crypto wallet platform Cryptonator has been seized by US and German law enforcement after the company failed to establish proper anti-money laundering controls.
Argentinian authorities arrested a Russian national involved in a multimillion-dollar money-laundering operation who accepted payments from illicit actors including North Korea’s Lazarus Group.
Legal
The DOJ’s Criminal Division has launched a whistleblower program to uncover and prosecute corporate crime focused on financial institutions, including cryptocurrency businesses.
Telegram CEO Pavel Durov was arrested in late August at Le Bourget airport outside of Paris, France with French prosecutors alleging that Telegram is being used for criminal purposes and that Telegram refused to share information or documents with investigators.
Scams
Jupiter, a decentralized exchange aggregator, identified a malicious browser extension that drained the wallets of several of their Solana users while sneaking past detectors.
Cthulu Stealer, a new malware-as-a-service sold for $500/month, has been discovered stealing crypto from places like MetaMask, Coinbase, and Binance.
A crypto whale lost $55.4M in DAI to a phishing attack after the attacker lured the victim into signing a TX to change the vault owner and then executed a TX to drain the vault.
The cofounder of the defunct crypto platform OmegaPro, Andreas Szakacs, was arrested in Turkey after being accused of defrauding investors through a $4B crypto Ponzi scheme.
Meet Up With Us
We’ll be at the following conferences in September. If you’d like to set up 1:1 time with our team, then reach out to sales@zellic.io for scheduling!
KBW 2024 — Seoul (September 1 - 7)
TOKEN2049 — Singapore (September 16 - 20)
Recent Zellic Audit Reports
SatLayer Pool Audit Report: SatLayer is a universal security layer building upon Babylon to enable Bitcoin to be restaked to secure AVS applications.
Paragons DAO Audit Report: Paragons DAO is a Web3 gaming community focused on enabling players and guilds to compete and maximize their rewards through financial tools, shareable assets, edutainment, and competitive opportunities.
Session Token Audit Report: Session Token is the cryptocurrency driving the Session communications ecosystem. This EVM-compatible token can be used to unlock premium features within the Session private messaging application.
Chirp Network Audit Report: Chirp is creating a unified wireless network for IoT and broadband by harnessing the power of decentralized blockchain technology.