Zellic Security Roundup: August '25
Volume 2, Issue 8
Welcome to the August edition of the Zellic Security Roundup, the monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month, we will delve into our blog post, which covers a new ZK-friendly hash function designed by a Zellic cryptographer, recently published Zellic audit reports, and the latest news in Web3 security.
Zellic Research & Writing
Below is a snippet from our blog post “Introducing Polocolo: A ZK-Friendly Hash Function for PLONK with Lookup” written by Zellic cryptographer BaarkingDog.
We’ll be introducing this newly designed ZK-friendly hash function and the motivation behind Polocolo’s design.
Polocolo is another lookup-based ZK-friendly hash function from a different design rationale. The name Polocolo derives from power residue for lower cost table lookup.
To map an input x ∈ Fp to a lookup table, the possible value of x must be constrained via preprocessing. The Bar function in Reinforced Concrete uses a base expansion method to apply a lookup table to an element of Fp: x ∈ Fp is decomposed into an n-tuple (x1,…,xn) ∈ Zs1×⋯×Zsn then each xi is passing through small S-boxes. Each component is then fed into an S-box via table lookup. The outputs from the S-boxes are combined again to define the corresponding output of the Bar function. However, base expansion is significantly expensive in most ZK settings.
To address this, I propose an alternative approach, dubbed the power residue method, which efficiently applies lookup tables to Fp elements for a large prime p(≈2256). A power residue↗ can be seen as a generalization of the Legendre symbol. When a positive integer m divides p−1, the m-th power residue of x is defined as
The m-th power residue takes m+1 distinct values, so each possibility can be an input to a lookup table T of size m+1.
Now our new S-box S: Fp→Fp is defined as
By appropriately choosing T, this S-box can be made bijective. Moreover, this S-box is of a high degree that requires only 14 PLONK gates — for example, when m = 1024, which is significantly fewer than 94 gates required for the Bar function from Reinforced Concrete. Using this S-box, I propose Polocolo, a new lookup-based ZK-friendly hash function.
In the News
Hacks
CoinDCX, India’s largest crypto exchange, was hacked for $44.2M after one of its internal operational accounts was compromised in a security breach.
Crypto exchange BigONE suffered a third-party attack targeting its hot-wallet infrastructure, which led to an estimated loss of $27M.
WOO X, a crypto trading platform, lost $14M after nine user accounts experienced “unauthorized withdrawals”.
CrediX Finance, a decentralized finance protocol, has disappeared following a $4.5M exploit that drained funds from the platform, also raising suspicions of an exit scam.
GreedyBear, a threat actor group, used 650 malicious tools and 100+ fake extensions to hack $1M in crypto through a new technique called “extension hollowing”.
TRM Labs did a deep dive into the Nobitex hack and “how the Iran-Israel conflict exposed Tehran’s grip on its crypto services”.
Arkham Intelligence uncovered a previously undisclosed heist of 127,426 Bitcoin, now worth $14.5B, from Chinese mining pool LuBian in December 2020.
Research
“Inside North Korea’s effort to infiltrate US companies” is a look into how thousands of North Korean IT workers have used stolen and made-up US identities to pose as Western developers, engineers, and consultants to send hundreds of millions of dollars a year to North Korean military programs.
“Crypto Policy Under Trump: H1 2025 Report” from Galaxy reviews the Trump administration’s “notable accomplishments, outstanding tasks, and potential obstacles through the first half of 2025”.
“Crypto and Blockchain Venture Capital — Q2 2025” from Galaxy reviews the trends of crypto VC activity during Q2 2025 in comparison to Q1 2025, along with prior bull markets.
Zellic Lead Security Researcher Nan Wang was recognized as the seventh-ranked Most Valuable Researcher under the Microsoft Researcher Recognition Program.
Scams
A large-scale malicious campaign was uncovered, involving 40+ fake Firefox extensions designed to steal cryptocurrency wallet credentials. These extensions impersonate legitimate wallet tools from platforms like Coinbase, MetaMask, Trust Wallet, and many others.
Attackers are reregistering the domains of abandoned dApps and using them to steal users’ funds, in what Coinspect calls “zombie dApps”.
Crypto Rover tagged Grok to select a winner for a giveaway, and Grok replied about Crypto Rover’s involvement in pump-and-dump schemes and refused to select a winner.
Legal
Roman Storm, the founder of Tornado Cash, has been convicted for “willfully conspiring to operate a money transmitting business that moved more than $1 billion in dirty money”. The defendant was found guilty following a four-week jury trial before US District Judge Katherine Polk Failla.
The Hellenic Anti-Money Laundering Authority carried out Greece’s first cryptocurrency seizure, blocking access to funds lifted from the $1.5B Bybit hack.
The Southern District of New York filed charges against Shakeeb Ahmed for the alleged embezzlement of $9M from a DeFi protocol based on Solana back in 2022. SDNY claimed the charges represented the “first-ever criminal case involving an attack on a smart contract”.
Crime
Terraform Labs co-founder Do Kwon pleaded guilty to conspiracy and wire fraud three years after the $40B collapse of the TerraUSD stablecoin.
Suspects John Woeltz and Williams Duplessie in the New York crypto kidnapping and torture case were granted bail, with their next court appearance scheduled for October 15th.
Jian Wen, a former takeaway worker, was convicted of helping to convert stolen cryptocurrency into cash, jewelry, and real estate. The Bitcoin at the heart of Wen’s case was bought with money scammed from 130,000 Chinese investors between 2014 to 2017.
An Arizona woman was sentenced to 8.5 years in prison for aiding North Korean hackers in infiltrating over 300 US crypto and tech firms, which resulted in $17M in illicit revenue.
The FBI has warned the public about Hacker Com, “one of three subsets of the growing and evolving online threat group known as The Com”. Hacker Com involves a broad community of technically sophisticated cybercriminals, some of whom are linked to ransomware-as-a-service (RaaS) groups.
Meet Up With Us
We won’t be traveling in August, but if you’d like to set up 1:1 time with our team, then reach out to sales@zellic.io for scheduling.
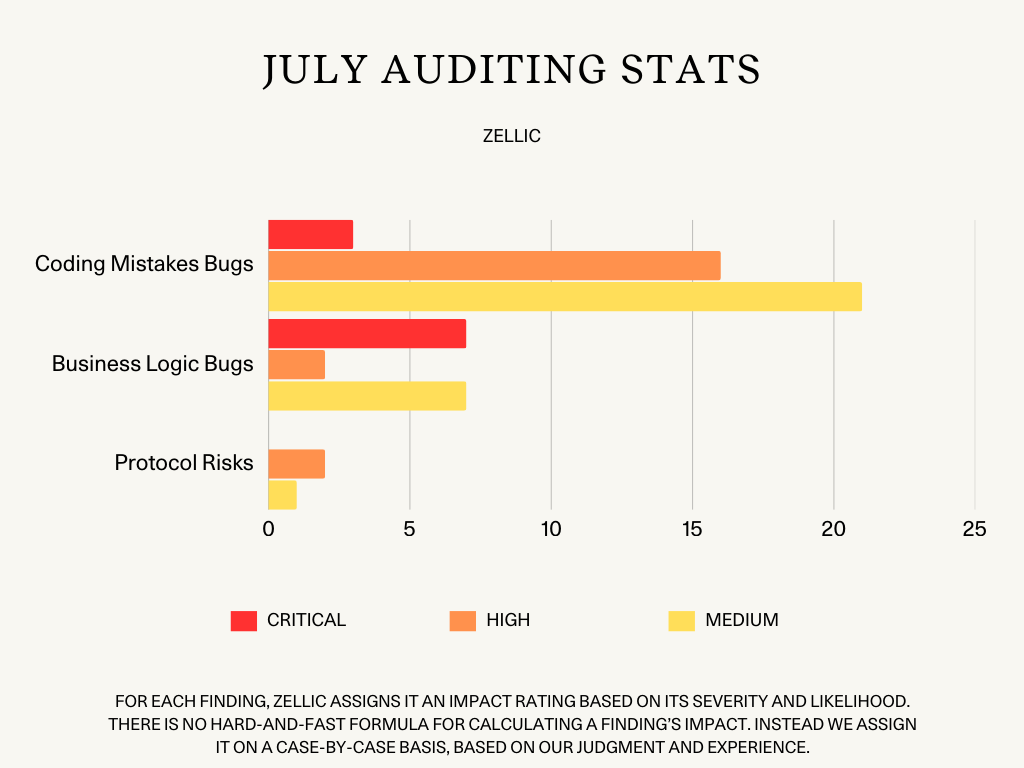
Zellic Auditing Stats
In July, Zellic auditors completed 22 audit engagements where they were able to uncover a total of 59 Critical, High, and Medium bugs:
10 Critical-level bugs
3 Coding Mistakes bugs
7 Business Logic bugs
20 High-level bugs
16 Coding Mistakes bugs
2 Business Logic bugs
2 Protocol Risks bugs
29 Medium-level bugs
21 Coding Mistakes bugs
7 Business Logic bugs
1 Protocol Risks bug
Recent Zellic Audit Reports
stake.link Audit Report: stake.link is the first-of-its-kind delegated liquid staking protocol for Chainlink Staking.
All in Bits Audit Report: AtomOne is a community-driven, constitutionally governed blockchain designed to prioritize security, decentralization, and innovation within the Cosmos ecosystem.
GTE Perp Audit Report: GTE is a perpetual futures protocol with a fully on-chain CLOB.
About Us
Zellic specializes in securing emerging technologies. Our security researchers have uncovered vulnerabilities in the most valuable targets, from Fortune 500s to DeFi giants.
Developers, founders, and investors trust our security assessments to ship quickly, confidently, and without critical vulnerabilities. With our background in real-world offensive security research, we find what others miss.
Contact us for real audits, not rubber stamps.