Zellic Security Roundup: December '24
Volume 1, Issue 11
Welcome to the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month will focus on our recent blog post, which covers three vulnerabilities discovered by a Zellic Security Researcher in the Dart/Flutter ecosystem, along with our recently completed audit reports and the latest news in Web3 security.
Cool Finds at Zellic
Below is a snippet from our blog post “Far From Random: Three Mistakes From Dart/Flutter's Weak PRNG” written by Zellic Security Researcher @Unblvr1.
We will be taking a look at the attack scenario for the first vulnerability covered in the post, the Dart SDK One-Click Exploit.
Many new adopters and testers of Flutter might start their journey by following the tutorial on the Flutter website. It will ask a user to install the required Dart SDK and create a new project in an IDE like Android Studio or Visual Studio Code. Once they have created their first project and are staring at their blank template, they might be tempted to look up the documentation online not knowing they are one click away from malicious users stealing files from their computer, or potentially executing code.
Flutter IDEs like Visual Studio Code and Android Studio rely on a persistent, long-running background process. That’s the Dart Tooling Daemon, or DTD for short. Once a Flutter workspace is opened, DTD will automatically start running in the background. This happens automatically when the IDE starts, and it is not triggered by building or running the project. From the package documentation itself,
The Dart Tooling Daemon is a long running process meant to facilitate communication between Dart tools and minimal file system access for a Dart development workspace.
When writing or running a Dart or Flutter application, in an IDE, the Dart Tooling Daemon is started by the IDE. It persists over the life of the IDE’s workspace.
Essentially, DTD is a websocket that listens on a random port. By connecting to it, users gain access to reading and writing files in the workspace directory, listing file directory contents, registering and listening to services, and listening to and posting events to streams. This websocket can be accessed from a browser, but it is somewhat secured by binding to a random port and a generated, random secret that has to be provided in the websocket path when connecting. From their own examples, the URI might look like this,
ws://127.0.0.1:62925/cKB5QFiAUNMzSzlb
where the random port is 62925 and the URI auth code is cKB5QFiAUNMzSzlb. In addition to this secret, there’s a second secret that is required for the special the API call setIDEWorkspaceRoots(secret, roots), which unlocks the capability for the clients to access any file on the computer — not just the ones in the workspace.
But how are these secrets generated? This all happens in dart_tooling_daemon.dart, where we extract only the relevant snippets:
static String _generateSecret() {
String upper = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ';
String lower = 'abcdefghijklmnopqrstuvwxyz';
String numbers = '1234567890';
int secretLength = 16;
String seed = upper + lower + numbers;
String password = '';
List<String> list = seed.split('').toList();
Random rand = Random();
for (int i = 0; i < secretLength; i++) {
int index = rand.nextInt(list.length);
password += list[index];
}
return password;
}
final String? _uriAuthCode = disableServiceAuthCodes ? null : _generateSecret();
final secret = _generateSecret();Turns out, these secrets are merely 32 bits. Let’s confirm by brute forcing the seed of the example URI.
$ time ./findseed.py cKB5QFiAUNMzSzlb
Recovered seed: 0xAA70CB0D
real 0m10.428s
user 0m10.242s
sys 0m0.006sThis isn’t great. A silver lining is that the two secrets are generated independently, so an attacker needs twice the brute force (33 bits) in order to recover both. But a huge downside is that the websocket can be accessed by JavaScript on any malicious website, completely without user interaction. The website can automatically brute force the port, followed by testing all four billion possible secrets. At this point, the website can list directory contents, extract and exfiltrate secret files from the workspace, or overwrite build scripts and GIT hooks to indirectly run arbitrary code. After recovering the second secret and changing the workspace roots, the same can be applied to all files that the current user has access to, for example in a typical stealer malware fashion. The same attack scenario applies to local processes that run under less privileged users, allowing privilege escalation.
In our report, we included a JavaScript implementation of the attack that runs when a developer visits a website. It brute forces the port, then starts a throttled scan to guess the authentication code. Such an attack takes some time to run, because browsers have a limit to how many concurrent websockets they allow. So in a real-life scenario, the attacker would need to put the malicious code on a website where the victim is likely to linger (e.g., a Flutter tutorial website, websites that stream video, have messaging services or similar). It is possible to make the attack persist through page clicks by using cookies or localStorage to store progress.
Zellic Research & Writing
Far From Random: Three Mistakes From Dart/Flutter's Weak PRNG
A look into how an unexpectedly weak PRNG in Dart led to Zellic's discovery of multiple vulnerabilities in the Dart/Flutter ecosystem.
Security Day presented by Archetype
Zellic CEO Luna Tong will be presenting at Archetype’s final Research Day of the year on Thursday, December 12th at Archetype HQ in NYC.
In the News
Research
DeFi Security 101 at DeFi Security Summit 2024 held a series of hands-on workshops and panels on various topics in Web3 security:
Succinct Co-Founder and CEO Uma Roy joined a recent ZK Whiteboard Session to review core components of zkVMs and provide analysis on real-world zkVM use-cases and tradeoffs:
a16z crypto released its third annual State of Crypto report, which covers “crypto’s rise as a hot topic policy, the many recent tech improvements to blockchain networks, and the latest trends among crypto’s builders and users”.
“From Prediction Markets to Info Finance” is a recent Vitalik blog that covers his interest in prediction markets and beliefs into why “prediction markets even as they exist today are a very useful tool for the world” and how “prediction markets are only one example of a much larger incredibly powerful category”.
Episode 345 of the ZK podcast featured Dan Boneh, Professor of Computer Science and Electrical Engineering at Stanford University. During the podcast, they discussed lattice-based SNARKs, ZK for content provenance, ZK in the FHE context, updates on ZK in ML, and more.
Legal
Following an FBI sting operation where agents created a token to lure market makers into illegal wash trading, Cointelegraph Magazine spoke with a panel of legal experts on potential copyright concerns, with allegations of improper use of open-source code, along with the application of traditional financial laws.
FTX sues Binance and former Binance CEO, “alleging that $1.8 billion was ‘fraudulently transferred’ by FTX management to Binance and its executives”. This lawsuit relates to Binance’s sale of its stake in FTX.
Members of the United States House of Representatives are demanding answers from the Treasury on why Tornado Cash is still operational following its sanction in August 2022.
The US Court of Appeals for the Fifth Circuit has ruled that the Treasury’s sanctions against Tornado Cash were unlawful and an overreach of authority, explaining that “since Tornado Cash’s smart contracts are ‘unchangeable and unremovable,’ they remain available for anyone”.
Heather “Razzlekhan” Morgan has been sentenced to 18 months in prison after laundering the stolen funds from the 2016 Bitfinex hack, led by her husband Ilya “Dutch” Lichtenstein.
A hacker drained a US government-controlled wallet of $20M on October 24th, which included funds from the 2016 Bitfinex hack
The US Department of Justice announced charges against five alleged hackers who targeted employees at American companies with phishing texts, allegedly stealing $6.3M in cryptocurrency from a single unnamed victim.
Crime
The FBI raided the home of Polymarket CEO Shayne Coplan following the US presidential election, where agents entered Coplan’s apartment demanding he turn over his devices. Coplan has not been arrested or charged.
A Devcon attendee was robbed in Bangkok by two assailants just days before the start of the conference, marking the latest in a series of security incidents involving conference attendees.
CEO of WonderFi, Dean Skurka, was the victim of a kidnapping and held for ransom in downtown Toronto. Skurka was released after a ransom of $1M Canadian dollars was paid; he was unharmed and police are undergoing an investigation.
South Korean police arrested 215 individuals linked to a crypto-investment scam ring that defrauded 15,304 victims, leading to losses exceeding $232M.
Hacks
October crypto losses reached $129.6M, with the largest incident involving Radiant Capital, where there was an estimated $53M in losses.
DEXX, a memecoin trading terminal, was hacked with total losses hovering around $30M, impacting at least 900 individual users.
Crypto exchange XT.com suspended withdrawals after a suspected $1.7M hack where on November 28th, XT cited the need for suspended withdrawals as “wallet upgrade and maintenance”.
Crypto casino Metawin was drained of ~$4M in tokens after an exploit to Metawin’s withdrawal system to attack its hot wallets on Ethereum and Solana.
DeltaPrime, a decentralized borrowing and investing ecosystem, suffered a $4.75M hack that affected pools on Arbitrum and Avalanche. This is DeltaPrime’s second hack since September.
Apple confirmed two vulnerabilities, credited to Google’s TAG, that were exploitable on Intel-based macOS systems. Apple urged users to apply the urgent iOS 18.1.1, macOS Sequoia 15.1.1, and the older iOS 17.7.2.
Scams
BlueNoroff, a North Korean threat actor, has targeted crypto-related businesses with new malware for macOS systems. Starting with a phishing email, “the malware deployed relies on a novel persistence mechanism on macOS that does not trigger any alerts on the latest versions of the operating system”.
BlueSky, a decentralized social media platform based on the AT protocol, has experienced a rise in crypto scams on its platform with the BlueSky safety team receiving 42,000+ reports in 24 hours.
The developers behind the Undead Apes NFT project have been found and pleaded guilty to charges of conspiracy to commit wire fraud and money laundering in what the US Department of Justice is considering a rug pull.
Meet Up With Us
We will not be traveling to any conferences in December. If you’d like to schedule 1:1 time with our team, reach out to sales@zellic.io.
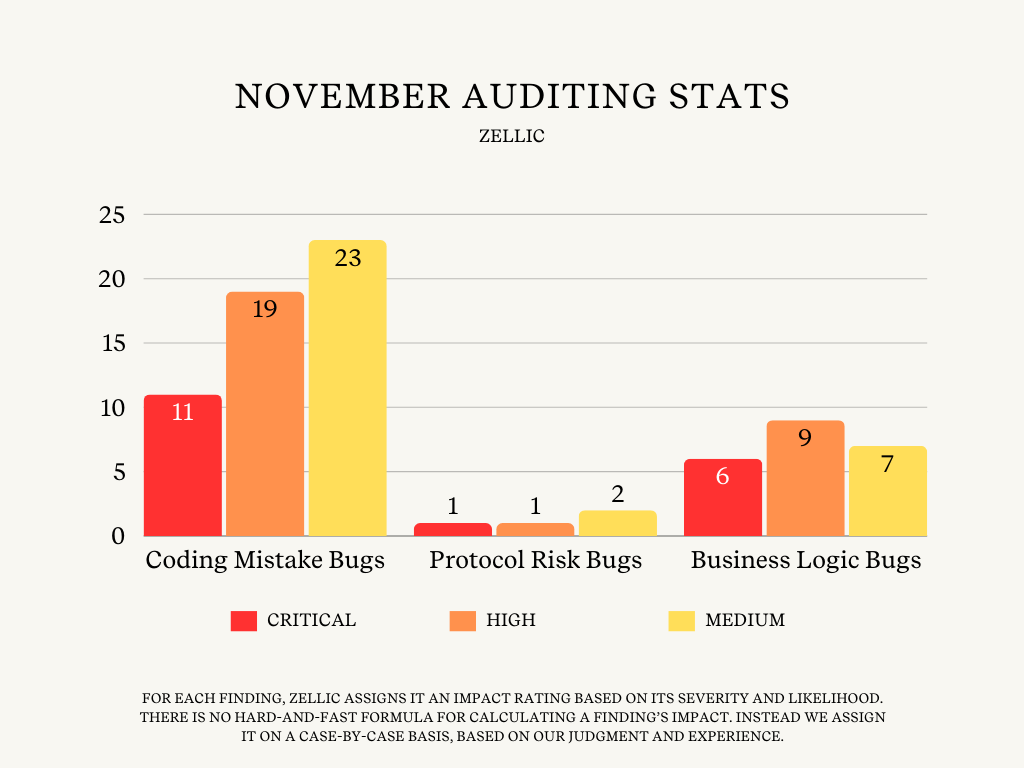
Zellic Auditing Stats
In November, Zellic auditors completed 32 audit engagements where they were able to uncover a total of 79 Critical, High, and Medium bugs:
18 Critical-level Bugs
11 Coding Mistakes bugs
1 Protocol Risks bug
6 Business Logic bugs
29 High-level Bugs
19 Coding Mistakes bugs
1 Protocol Risks bug
9 Business Logic bugs
32 Medium-level Bugs
23 Coding Mistakes bugs
2 Protocol Risks bugs
7 Business Logic bugs
Recent Zellic Audit Reports
Facet Node Audit Report: Facet Node is a specialized adaptation of the standard Ethereum node infrastructure, designed to facilitate the execution of Facet’s off-chain compute.
SolBLS Audit Report: SolBLS is a Solidity library for efficient BLS signature verification over the BN254 curve, optimized for on-chain verification.
Grug Audit Report: Grug is an execution environment for blockchains. The scope of this audit is the state commitment scheme that Grug uses, the Jellyfish Merkle Tree (JMT).
InfiniCard Vault Audit Report: InfiniCard Vault is a centrally managed contract platform designed to efficiently manage and grow assets through various strategies.