Zellic Security Roundup: March '24
Volume 1, Issue 2
Welcome to the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
Cool Finds at Zellic
What’s the finding? The finding is a Denial of Service (DOS) of the cross-chain withdrawal mechanism.
Audit: Orderly Network
Timeline: Orderly Network, a unified trading infrastructure for decentralized exchanges, approached Zellic to perform a security assessment centered around Orderly’s infrastructure. During the security assessment, nine findings (one critical, four high impact, three medium impact, and the remaining finding informational) were uncovered. Below is a look at a specific finding that was uncovered during this security assessment.
Description of the bug: Withdrawals work in a cross-chain manner. The user sends a withdrawal request via the off-chain architecture, which is then processed by the OperatorManager and forwarded to the Ledger. The Ledger then freezes the user balance on the sending side of the chain and forwards a cross-chain message onto the destination chain where the withdrawal is finalized via the Vault contract. At the time of the security assessment, there was no accounting on which chain the user originally deposited the funds from, and this can lead to a situation where the user is unable to withdraw their funds on the desired, initial deposit chain.
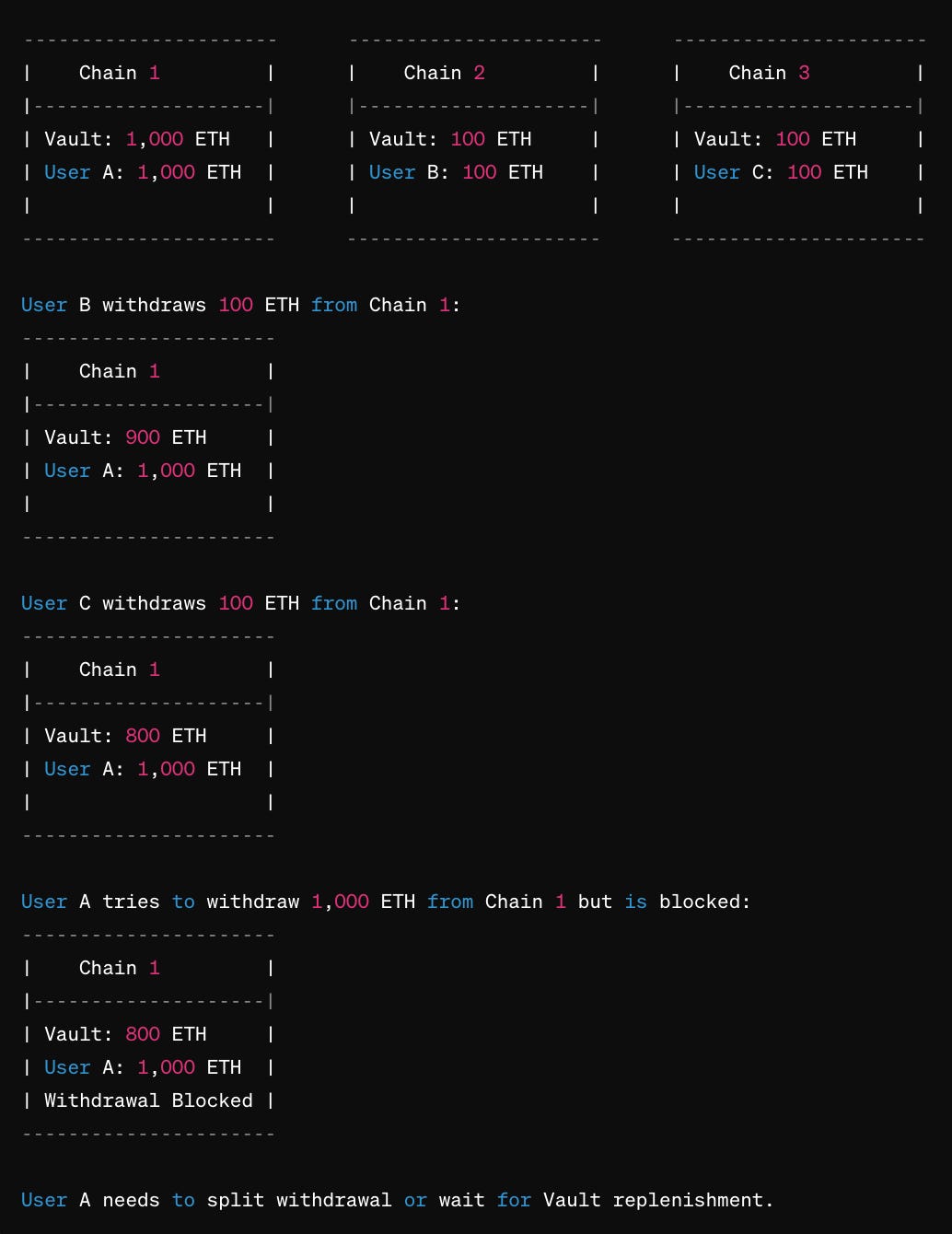
Imagine we have users A, B, and C and chains 1, 2, and 3:
User A deposits 1,000 ETH on Chain 1, User B deposits 100 ETH on Chain 2, and User C deposits 100 ETH on Chain 3.
User B withdraws 100 ETH on Chain 1, and User C withdraws 100 ETH on Chain 1. There is now only 800 ETH left in the Vault contract on Chain 1.
User A tries to withdraw 1,000 ETH on Chain 1, their original chain, but the withdrawal is blocked because the Vault contract on Chain 1 does not possess enough funds to cover the withdrawal, as User B and User C have already withdrawn their funds on Chain 1, rather than on their original chain.
User A is forced to split their withdrawal across multiple chains or wait for the Vault contract to be replenished with funds from other users.
How we found the bug: Cross-chain protocols typically imply asynchronous states, which are complicated to reason about. One can imagine a whiteboard that’s divided into multiple slices, with a small circle drawn inside one of them. If you were to move that circle from one slice to the other, you would first have to erase it from the current slice — let’s call it slice A — and draw it again in slice B. Cross-chain messages require a similar interaction, where an off-chain component is responsible for transitioning a particular object from one chain to the other.
In such scenarios, the developer must not only maintain the integrity of the object that’s being transferred but also maintain the overall security and sanity of the transfer. That being said, it’s essential that one carefully assesses what invariants need to hold on all sides of a transaction, whether it’s the origin or the destination chain.
When reviewing cross-chain protocols, especially those that need to maintain an asynchronous state between the involved chains, we prioritize very high-level, 10,000-yard overviews:
What should each of the transfers look like?
What are the objects involved?
Have the states that should change during a transfer as well as the functions that rely on those states been tracked?
Do the states as well as the functions that rely on those states work as intended?
This approach led to the discovery of the bug, as it became apparent that if a user were to transfer back to their original deposit chain, there could be a case of not enough funds being left available.
Impact of the bug: The aforementioned scenario can lead to a situation where a user is unable to withdraw their funds on the desired chain, potentially leading to loss of funds as the user would need to perform additional transactions to withdraw their funds on the desired chain, incurring further risks from the third-party protocol they are using to perform the cross-chain swap.
Fix for the bug: We recommended that the OperatorManager contract keeps track of which chain the user originally deposited their funds from and only allows withdrawals to be processed on that particular chain. This required a change to the Ledger contract to allow the OperatorManager to specify the chain on which the withdrawal should be processed and keep track of the original chain the user deposited their funds. This recommendation was implemented by Orderly Network following the security assessment.
Big thanks to the Orderly Network team for their close collaboration during this security assessment!
Zellic Research & Writing
Signal’s Usernames and Ristretto Hashes
A look into Signal’s use of Ristretto hashes and zero-knowledge proofs for usernames.
MPC From Scratch: Everyone Can Do It!
Building an implementation of garbled circuits from the ground up.
Breaking Down the Puzzles in ZK Hack IV
A look into the three puzzles solved by the Zellic cryptography team for ZK Hack IV.
In the News
The Ethereum Foundation has opened its first ZK Grants Round in collaboration with Aztec, Polygon, Scroll, Taiko, and zkSync with a total, shared prize pool of $900,000.
The White House Office of the National Cyber Director released a report calling on the technical community to reduce the attack surface in the digital ecosystem by adopting memory-safe programming languages.
Apple introduced PQ3, “a groundbreaking post-quantum cryptographic protocol”, to iMessage, which according to Apple “has the strongest security properties of any at-scale messaging protocol in the world”.
Polygon and StarkWare have joined forces to build a new type of cryptographic proof called Circle STARKs, with the goal of making transactions faster and cheaper.
The Security Alliance (SEAL) made its public launch along with the RFC for a Whitehat Safe Harbor Agreement. A proposed legal and technical framework has been developed to provide safe harbor to whitehats who are in a position to protect protocols under active exploitation.
Samczsun, the Head of Security at Paradigm, was recently interviewed on the Unchained Pod to discuss the origin of the Security Alliance (SEAL), the Whitehat Safe Harbor Agreement, and more.
Zellic joined LayerZero to discuss the LayerZero V2 audit for their latest installment of the LayerZero Lounge.
Meet Up With Us
Zellic will be participating in Magna’s inaugural Token Launch School, a one-day virtual boot camp that will explore all aspects of launching a token.
Zellic Co-Founder Stephen Tong will be participating in the Program Committee for the USENIX WOOT Conference on Offensive Technologies (WOOT '24), an annual event that brings together researchers and practitioners across all areas of computer security.
Recent Zellic Audit Reports
Chateau Capital Audit Report: Chateau Capital is a DeFi protocol for real-world equity, debt, and derivatives.
SupSwap Audit Report: SupSwap is a cost-efficient liquidity layer on Mode Network.
SyncSwap Aqua Pool Audit Report: Aqua Pool is a pool with automated concentrated liquidity to support exchange between two tokens on Ethereum ZK rollup networks (such as zkSync Era, Linea, and Scroll).
Origami Finance Audit Report: Origami Finance is a protocol that provides targeted leverage for any whitelisted liquid-staking strategy through a simple vault UX.