Zellic Security Roundup: February '24
Volume 1, Issue 1
Welcome to the first edition of the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
Cool Finds at Zellic
What’s the finding? The
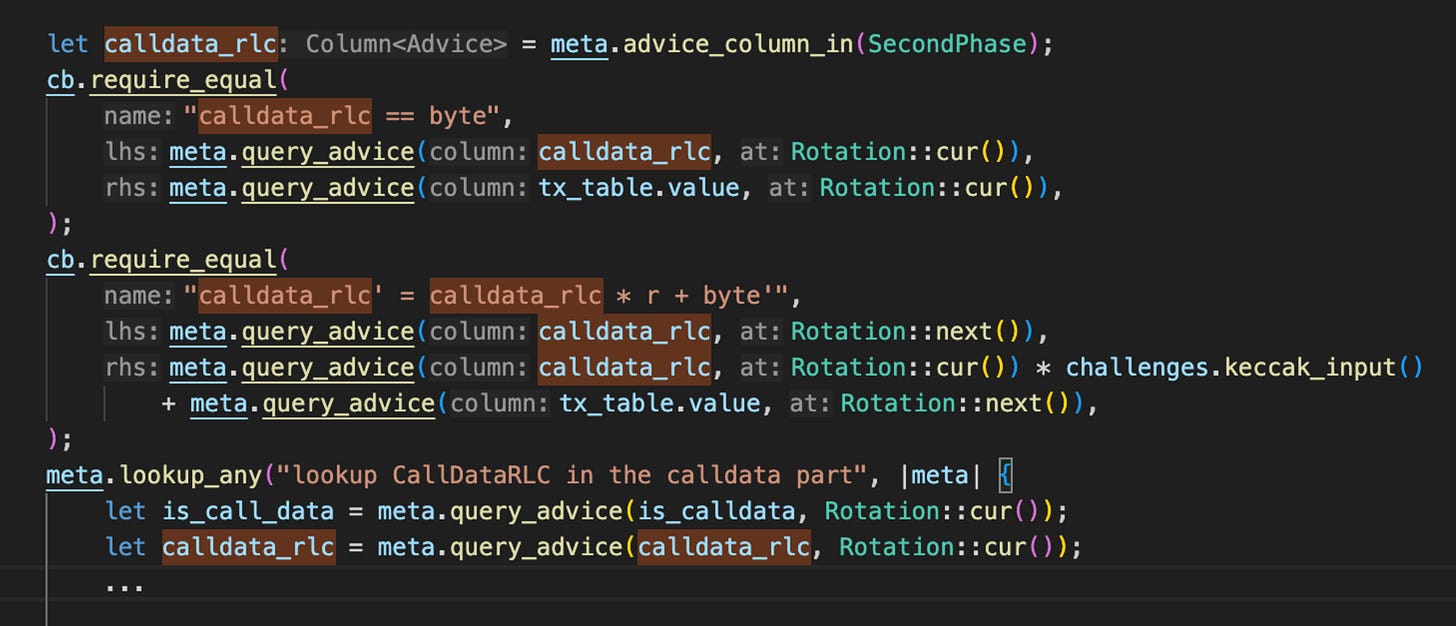
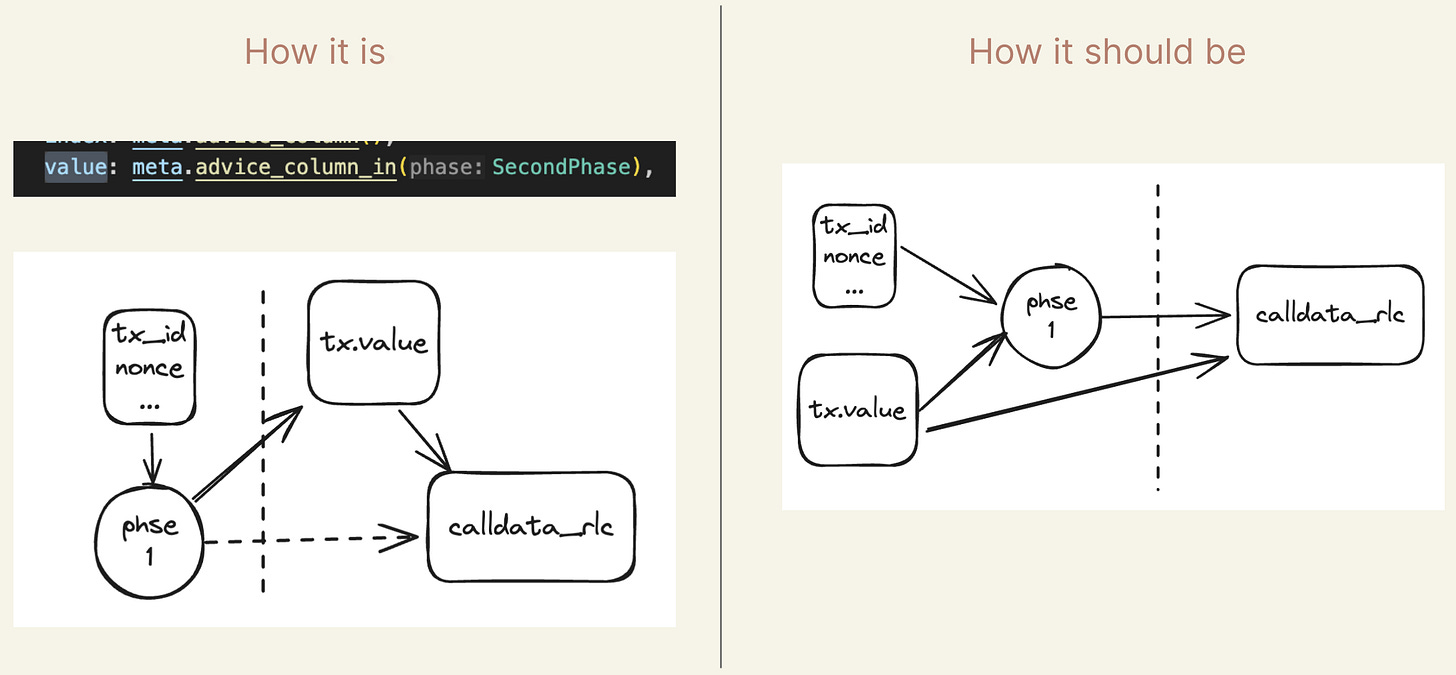
CallDataRLCvalue in the fixed assignments was not validated against the actual calldata in the TX circuit.
Audit: Scroll zkEVM - Part 2
Timeline: Scroll approached Zellic before the launch of Scroll Mainnet to perform a security assessment of their ZK circuits. Our cryptographers, in collaboration with Allen Roh of KALOS, conducted a security assessment where a total of 30 findings (13 critical, 8 high impact, 4 medium impact, 1 low impact, and the remaining informational) were uncovered. All of the findings were acknowledged and fixed by Scroll before their mainnet launch. Below is a look at a specific bug that was found during this security assessment.
Description of the bug: There was no check to ensure that the calldata in the dynamic part of the transaction circuit is the same as the calldata parsed in the RLP circuit. This meant that the prover could place any arbitrary calldata in the TX table as long as the calldata length remained the same and could, for example, change the address of an ERC-20 transfer transaction.
How we found the bug: Halo2 circuits are often composed of various tables that compute different functionalities. In the case of this bug, we have an RLP table that performs the decoding of the transaction and the TX table, which parses the transaction data fields. These tables often share the same data, but they are stored in different places. In this instance, there was the calldata from the RLP table and the calldata in the TX table.
The developer has to ensure that there are checks and constraints to make sure that these values are the same. When auditing Halo2 code, we look for these kinds of relations as we look at the sources of data for a table and ensure that the cells are constrained to be from a certain source. This led to the discovery of this bug as we noticed that the calldata in the TX table was not constrained properly.
Impact of the bug: A malicious prover could modify the execution of a signed transaction from a user and change the calldata arbitrarily.
Fix for the bug: We recommended adding the check of the consistency between the CallDataRLC and the calldata part of the TX circuit layout via a lookup argument.
We want to give a special thanks to the excellent team at Scroll for their close collaboration!
Zellic Research & Writing
What Is a ZK Audit?
A look into the ZK audit process and the techniques that the best ZK auditors use to examine ZK circuits.
What Are Elliptic Curve Pairings?
An introduction to what pairings are and how they are motivated, focusing particularly on elliptic curve pairings.
Finding a Critical Vulnerability in Astar
A look into how two Zellic security researchers helped fix a critical vulnerability in the Astar Network.
CSPRNGs: How to Properly Generate Random Numbers
An in-depth guide to secure random number generation and how to properly generate random numbers using cryptographically secure pseudorandom number generators.
In the News
“Guarded Launch: Protecting Glow Users Against Hacks” is an overview of Glow Protocol’s new guarded launch concept, which allows a protocol to launch, demonstrate market viability, and then raise the hundreds of thousands of dollars required for a deep security review.
“An Open Letter to the Manufacturers and Designers of Crypto Wallets” is a list of suggestions and ideas gathered by the author (Officer’s Notes) that could help curb the number of attacks on wallets from “what appear to be straightforward attacks”.
Etherscan is awesome, but it is also a critical point of failure for Ethereum as the reliance on Etherscan could attract malicious actors to exploit it as an attack vector on the Ethereum community.
EigenLayer is introducing a new security model that will let users buy “insurance” (attributable security that gives actively validated services [AVS] a claim on a certain amount of restaked capital that it can seize and redistribute in the event something goes wrong) to reduce collateral damage suffered by EigenLayer users in the event they are successfully hacked.
Ripple Co-founder Chris Larsen had his personal Ripple accounts compromised for ~$112M XRP as he said that there had been “unauthorized access to a few of my personal XRP accounts”.
A total of $1.84B was lost in Web3 across 751 security incidents in 2023, a 51% decrease from the $3.7B lost in 2022.
Zellic Co-founder Stephen Tong participated in the analysis, code review, and ongoing work during the follow-up of Radiant Capital’s flash-loan–based exploit.
A write-up from Zellic Co-founder Jazzy was on the CTF challenge he created for Curta, involving CREATE2 and metamorphic deployments.
Meet Up With Us
ETHDenver 2024 (Feb. 28 – Mar. 3): We’ll be at ETHDenver! If you’d like to set up 1:1 time with our team in Denver, reach out to sales@zellic.io for scheduling.
Zellic-hosted side events:
ATOMDenver² on February 28th (link to registration with additional details)
Recent Zellic Audit Reports
Orderly Network Audit Report: Orderly Network is an omnichain trading infrastructure that unifies liquidity across blockchains.
Biconomy Secp256r1 Audit Report: Biconomy Secp256r1 implements ECDSA signature verification on the secp256r1 curve.
Nukem Loans Audit Report: Nukem Loans is a protocol revolving around a set of smart contracts that enhance meme communities by creating their own token economy through the establishment of permissionless lending markets created by lenders.
Mysten Labs (GotSui) Audit Report: GotSui is a browser-based application that makes sending SUI as easy as sending a link.