Zellic Security Roundup: July '25
Volume 2, Issue 7
Welcome to the July edition of the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month, we will dive into a major pitfall of BLS signatures and how to prevent it, a look into Zellic’s partnership with Injective, and the latest news in Web3 security.
Zellic Research & Writing
Below is a snippet from our blog post “What Are BLS Signatures and How Do They Work?” written by Zellic Cryptographer Sylvain Pelissier.
We’ll be looking at the pitfall of multi-signatures and how to prevent it via proof of possession.
The Pitfall of Multi-signatures
Multi-signatures come with a serious potential pitfall called rogue-key attacks. Let’s illustrate how this kind of attack works.
Let’s suppose an honest user has a public key pk0. Then, an attacker who has previously seen pk0 can choose their public key as pk1 = sk1⋅G1 − pk0. The attacker would not know the private key associated to the public key. However, the multi-signature verification would give the following:
Only sk1 is needed to sign a message resulting in a valid multi-signature, even though the first user may not have signed it. This is easily generalized to any number r of honest users by choosing the rogue key, being
This is a dangerous threat since, in our previous AVS example, a malicious aggregator that would have previously registered a rogue key could send aggregate signatures that were not signed by the validators but still will be accepted by the contract. This would lead to having validators being slashed even if they did not misbehave.
Proof of Possession
To prevent a rogue-key attack, a common method is to request users to prove they know the private key matching their public key. Thus, in a first registration step, the user is requested to register their public key together with a proof of possession π such that
Basically, the user is requested to sign their public key or any other identification message. However, the hash function ~H~ used in the proof has to be different from the one used by the aggregated signature verification. In practice, the construction of ~H~ is achieved by using domain separation as explained in the IETF draft↗.
Then the aggregator registers public keys by verifying the proof of possession π with the BLS verification algorithm using the other hash function ~H~.
In the EigenLayer contract, the proof of possession is verified by the registerBLSPublicKey function:
function registerBLSPublicKey(
address operator,
PubkeyRegistrationParams calldata params,
BN254.G1Point calldata pubkeyRegistrationMessageHash
) external onlyRegistryCoordinator returns (bytes32 operatorId) {
// [...]
// gamma = h(sigma, P, P', H(m))
uint256 gamma = uint256(keccak256(abi.encodePacked(
params.pubkeyRegistrationSignature.X,
params.pubkeyRegistrationSignature.Y,
params.pubkeyG1.X,
params.pubkeyG1.Y,
params.pubkeyG2.X,
params.pubkeyG2.Y,
pubkeyRegistrationMessageHash.X,
pubkeyRegistrationMessageHash.Y
))) % BN254.FR_MODULUS;
// e(sigma + P * gamma, [-1]_2) = e(H(m) + [1]_1 * gamma, P')
require(BN254.pairing(
params.pubkeyRegistrationSignature.plus(params.pubkeyG1.scalar_mul(gamma)),
BN254.negGeneratorG2(),
pubkeyRegistrationMessageHash.plus(BN254.generatorG1().scalar_mul(gamma)),
params.pubkeyG2
), "BLSApkRegistry.registerBLSPublicKey: either the G1 signature is wrong, or G1 and G2 private key do not match");
operatorToPubkey[operator] = params.pubkeyG1;
operatorToPubkeyHash[operator] = pubkeyHash;
pubkeyHashToOperator[pubkeyHash] = operator;
emit NewPubkeyRegistration(operator, params.pubkeyG1, params.pubkeyG2);
return pubkeyHash;
}The same trick as before for public key and signature verification is applied here as well. But as explained before, the hash is computed differently. The function pubkeyRegistrationMessageHash is used:
function pubkeyRegistrationMessageHash(address operator) public view returns (BN254.G1Point memory) {
return BN254.hashToG1(
_hashTypedDataV4(
keccak256(abi.encode(PUBKEY_REGISTRATION_TYPEHASH, operator))
)
);
}The hash function uses a custom domain separator PUBKEY_REGISTRATION_TYPEHASH to build a different hash function, and the message is simply the operator address. After registration, the public key is added to the contract. We can verify its value by calling the getRegisteredPubkey function. Here is an example of a BLS public key registered for EigenDA AVS:
It is important to have a different hash function for this part. Let’s see what would happen if we used the same hash function H as used in the BLS signature. This is the proof of possession:
If the attacker is able to request the aggregate signature σagg of pkagg, then they are able to register the rogue key
by sending the proof:
This would then allow the attacker to do a rogue-key attack, as described before. Thus, it is essential to use domain separation.
Proof of possession is basically a BLS signature. However, it is also not advisable to use multi-signatures during the proof-of-possession step, for example, to register multiple public keys for a single participant. If so, the participant would achieve a splitting zero attack↗. In this case, the participant could register keys that would cancel out when summed together and could bypass the proof of possession.
Check out the full blog post here!
Client Success With Zellic
How Zellic Shapes the Injective Ecosystem: From Audits to Validator
In 2018, Eric Chen and Albert Chon founded and built a decentralized trading platform with the vision of addressing the limitations of existing platforms while providing the speed and efficiency required by traditional finance. They called this platform Injective.
After years of rapid growth and with a vision of solving the most common crypto trader issues, the team realized they needed to fix the base layer. This ultimately culminated in launching the Injective blockchain in October 2021. In 2024, Injective called on Zellic for their expertise to conduct security audits for Injective Core and its ecosystem projects.
Now, with over 100 projects in the Injective ecosystem and a network-wide total of 57,000,000+ staked INJ, Zellic has become the number one validator by voting power.
And by converting the rewards earned from its validator operations to audit credits to be spent on security reviews, Zellic has further committed itself to being an integral part of the Injective ecosystem’s security infrastructure.
Zellic is one of the most well-known names in the industry. We work with Zellic to get top security audits but also to provide assurances to our partners that our codebase is secure. — Eric Chen, Co-Founder and CEO of Injective Foundation
How Zellic Auditors’ Unmatched Security Expertise Is Essential to the Injective Ecosystem
Injective searched for a security auditor who could meet their timelines and technical needs and conduct a continuous audit.
Hearing about Zellic from other partners, Injective was impressed by Zellic’s stringent auditing process. They received their first Zellic audit in Q2 2024 on their exchange module.
This audit was crucial as the exchange module is at the heart of the Injective chain and enables fully decentralized spot and derivative exchange. The exchange module enshrines a central limit order book (CLOB) within the Injective chain itself. This architecture introduces complexity and uniqueness, which made it paramount for Injective to work with a best-in-class auditor like Zellic as the exchange module is one of the most important features and offerings of the chain.
Zellic’s expertise made them not only fully equipped but ideal for the task.
Zellic has demonstrated exceptional expertise and a deep understanding of domain-specific and complex code, enabling them to conduct comprehensive and insightful security assessments. — Eric Chen, Co-Founder and CEO of Injective Foundation
Pleased with the thoroughness of the audit, the Injective team made Zellic a staple security auditor for new contracts and modules.
Beyond audits for Injective Core, Zellic is committed to securing the Injective ecosystem as a whole, conducting security audits for Injective ecosystem projects like TruFin.
How Zellic Supports Injective’s Safety, Development, and Innovation as a Validator
Zellic operates one of the most secure and highly redundant validators. Their team is 24/7 available for incident response at any hour. — Eric Chen, Co-Founder and CEO of Injective Foundation
With Zellic’s background in real-world offensive security research and track record of security audits for Injective Core and ecosystem projects, Injective put their trust in Zellic to become an indispensable partner, ensuring the security and robustness of Injective’s core network infrastructure.
Zellic’s validator operations team is made up of former DevSecOps professionals from Fortune 500s, enterprise blockchain infrastructure protocols, and industry titans like Chainlink.
Leveraging their experience in establishing and securing mission-critical infrastructure, in tandem with a security-first approach, Zellic has become the number one validator on Injective by voting power.
But Zellic also uses this opportunity to continue to give back to the Injective ecosystem.
The rewards earned from the delegation provided by both Injective and community stakers are given back as audit credits to help subsidize the cost of audits for Injective Core and its ecosystem projects. This virtuous cycle enables Injective to continue developing and innovating by ensuring the safety of new core protocol developments and supporting novel protocols introduced by Injective’s ecosystem projects.
This dedication to Injective led Zellic to be included in the first cohort of the Injective Validator Rebate Campaign. This campaign, announced on May 27th, 2025, is a strategic initiative designed to incentivize delegators with idle or inactive INJ to stake with validators who have consistently demonstrated their commitment to the Injective ecosystem.
In the campaign announcement, Injective said, “[Zellic] represent[s] the gold standard in blockchain infrastructure — [Zellic] doesn’t just validate transactions but actively shape[s] the ecosystem’s technical and strategic direction”.
In the News
Hacks
AlexLab, Bitcoin’s self-proclaimed finance layer, was hacked in a $16M+ liquidity siphon on June 6th, just over a year after losing $4.3M to a compromised private key.
According to research from TRM Labs, crypto private-key exploits and front-end compromises have accounted for the majority of the $2.1B in crypto lost to attacks in H1 2025.
Predatory Sparrow, an Israel-tied hacker group, stole at least $90M from Iran’s largest crypto exchange, Nobitex, over multiple transactions. Following the attack, “Nobitex’s entire source code, infrastructure documentation, and internal privacy R&D were leaked online”.
ZkLend is shutting down, including the delisting of its native Zend token from a few major exchanges, following a $9.5M exploitation earlier this year.
ResupplyFi, a stablecoin protocol, confirmed a security breach in its wstUSR market, which led to ~$9.6M in losses.
Research
Code4rena will be running audit contests for free going forward in an effort to help raise the bar for the entire crypto industry. High platform fees add friction for both sides. We’d rather focus on helping more builders access top-notch security and helping more auditors get paid for great work. That’s why we’ll be doing all of our contests for zero platform fees, indefinitely.
“Feeling Blue(Noroff): Inside a Sophisticated DPRK Web3 Intrusion” provides a detailed analysis of several new pieces of malware used by North Korean APT subgroup tracked as TA444, also known as aka BlueNoroff, Sapphire Sleet, COPERNICIUM, STARDUST CHOLLIMA, or CageyChameleon.
Telegram banned black markets that sold tens of billions of dollars in crypto scam services, but a new report shows how smaller markets have grown to almost fill the void left behind by the two biggest black markets, Haowang Guarantee and Xinbi Guarantee.
Koi Security discovered a critical vulnerability in an open-source VS Code extensions marketplace which provides attackers full control over the entire extensions marketplace, and in turn, full control over millions of developer machines.
Scams
Citibank has been sued by a self-claimed victim of a crypto romance scam, alleging the bank ignored red flags that allowed scammers to make off with $20M.
The Justice Department announced the largest-ever US seizure of crypto ($225.3M USDT) linked to pig-butchering scams across a network of at least 400 suspected victims worldwide. Coinbase’s threat-intelligence team publicly announced that it had “worked shoulder-to-shoulder” with agents for four months.
Legal
The Department of the Treasury’s Office of Foreign Asset Control (OFAC) sanctioned pig-butchering organization Funnull Technology Inc. and its administration Liu Lizhi, after Funnull was linked to over $200M in US victim-reported losses.
The California Department of Financial Protection and Innovation (DFPI) announced that it has entered into a consent order with Coinme, Inc., a crypto kiosk operator, for noncompliance with the state’s Digital Financial Asset Law. Under the consent order, Coinme has agreed to pay a $300,000 penalty.
Crime
The 24-year-old French-Moroccan citizen who has been suspected of orchestrating a string of high-profile crypto kidnappings in France has been arrested in Morocco.
US federal prosecutors charged a 25-year-old British man known as IntelBroker with leading a global cybercrime operation that stole sensitive data from dozens of companies, resulting in over $25M in damages.
Meet Up With Us
We won’t be traveling in July, but if you’d like to set up 1:1 time with our team, then reach out to sales@zellic.io for scheduling.
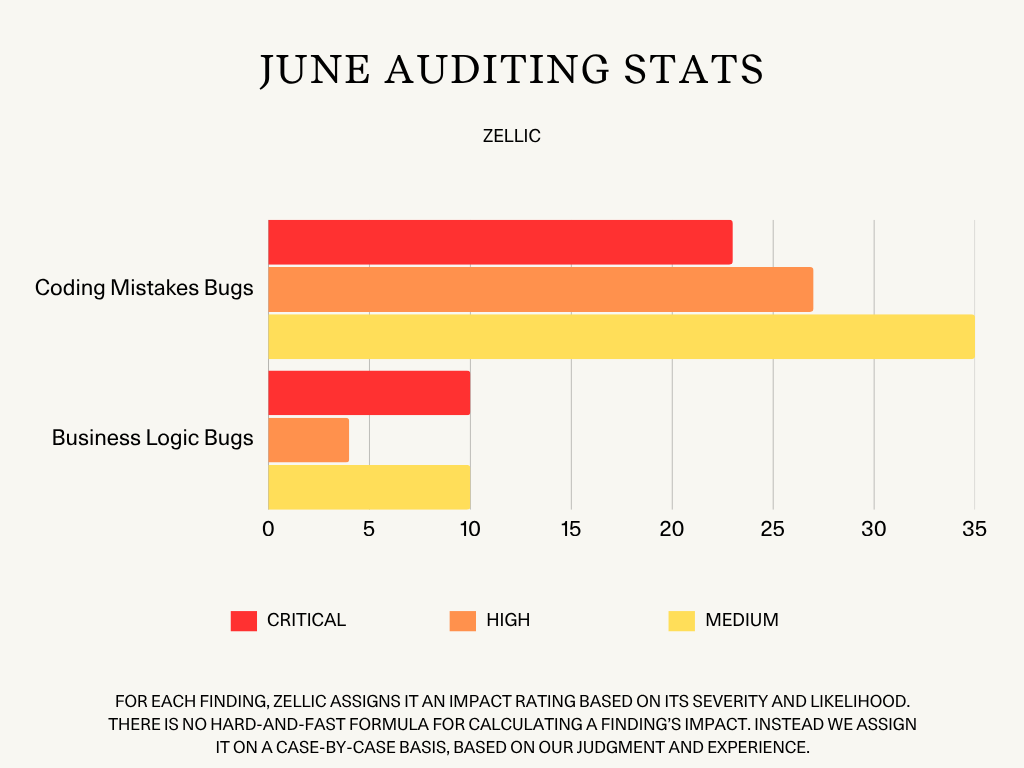
Zellic Auditing Stats
In June, Zellic auditors completed 33 audit engagements where they were able to uncover a total of 111 Critical, High, and Medium bugs:
33 Critical-level bugs
23 Coding Mistakes bugs
10 Business Logic bugs
33 High-level bugs
27 Coding Mistakes bugs
4 Business Logic bugs
2 Protocol Risks bugs
45 Medium-level bugs
35 Coding Mistakes bugs
10 Business Logic bugs
Recent Zellic Audit Reports
OpenZeppelin Cairo Contracts Audit Report: A library for secure smart contract development written in Cairo for Starknet, a decentralized ZK Rollup.
Garden Move Deploy Audit Report: Garden Finance is the fastest Bitcoin bridge, enabling cross-chain Bitcoin swaps in as little as 30 seconds.
DexFi Factory Audit Report: DexFi offers an ecosystem of financial products designed to empower users and simplify the DeFi experience.
About Us
Zellic specializes in securing emerging technologies. Our security researchers have uncovered vulnerabilities in the most valuable targets, from Fortune 500s to DeFi giants.
Developers, founders, and investors trust our security assessments to ship quickly, confidently, and without critical vulnerabilities. With our background in real-world offensive security research, we find what others miss.
Contact us for real audits, not rubber stamps.