Zellic Security Roundup: July '24
Volume 1, Issue 6
Welcome to the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month will focus on a bug in our recent security assessment of Singularity, our recent writing on the security and pitfalls of fully homomorphic encryption, and the latest news in Web3 security.
Cool Finds at Zellic
Audit: Singularity
Timeline: Singularity is a KYB/KYC-permissioned institutional DeFi access layer that provides access to popular protocols for on-chain participants to transact with commercial confidentiality. During the assessment period, Zellic uncovered 24 findings (eight critical, three high impact, five medium impact, three low impact, and the remaining informational). This is a look at one of the findings.
Description of the bug: Funds held by users in the Singularity dark pool can be in the form of ETH, ERC-20 tokens, or ERC-712 tokens. Users can deposit funds into the dark pool and withdraw them as well as transact within the dark pool or with external DeFi platforms such as Uniswap. For bookkeeping of these funds, notes are used that consist of three fields:
The
assetfield is used for the address of the token contract or a special value in the case of ETH.The
amountfield stores the amount of ETH or ERC-20 tokens in those cases or the NFT token ID in the case of ERC-712 tokens.The
footerfield stores a hash of a random value rho and the public key. The usage of this field is not relevant to this finding.
These notes are stored on chain in a single Merkle tree. As the ETH, ERC-20, and ERC-712 notes are not domain-separated, the possibility of using actions intended for one note type for a note of the other type is possible.
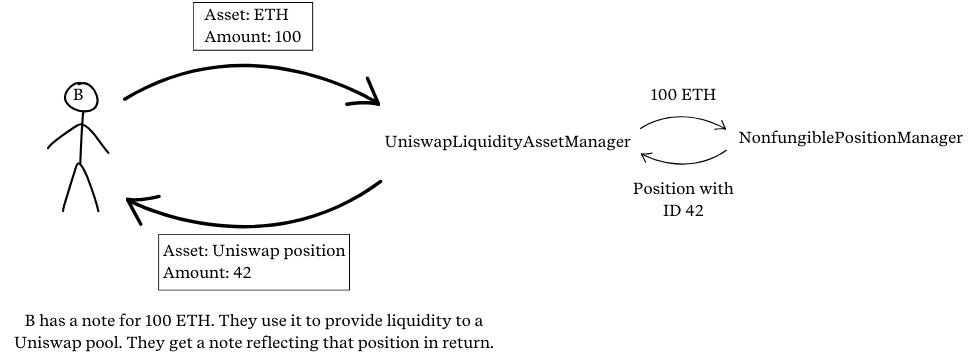
This leads to the possibility of the following kind of attack in which an attacker, A, can steal a liquidity position from another user, B:
B provides liquidity to some Uniswap pool via the UniswapLiquidityAssetManager. A position NFT with a certain token ID, say token ID
b, gets minted, and a position note in thedark poolreflecting that NFT is returned to B. Note that while the identity of B is protected, the token ID and amount of funds used for the position, as well as the pool interacted with, is visible on chain.
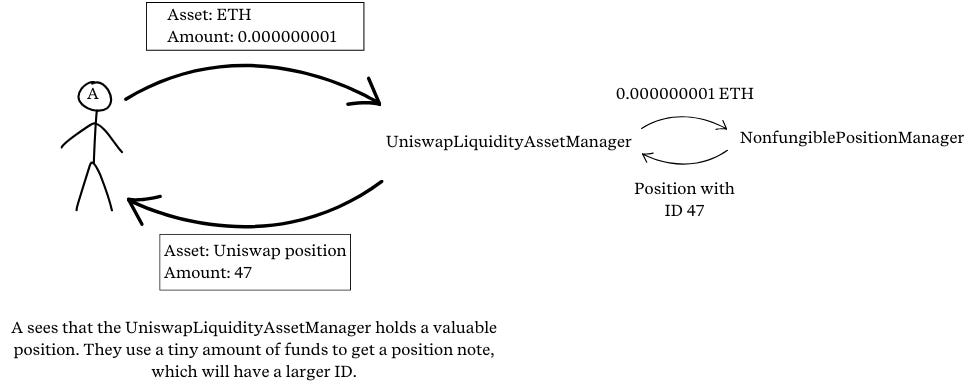
The attacker A also provides liquidity to a Uniswap pool while using a tiny amount of funds (thus, this step costs the attacker nearly nothing), receiving a position note corresponding to a position NFT with token ID
a. In practice, on minting of new position NFTs, the NonfungiblePositionManager increments the IDs. So it will hold thata > b.
The attacker A then calls
split, using their position note as input. Thesplitaction assumes a fungible type of note and interprets the second field as an amount. The attacker can thus usesplitto split the note into two, one where theamountfield holds the value b and one in which it holds the valuea-b.
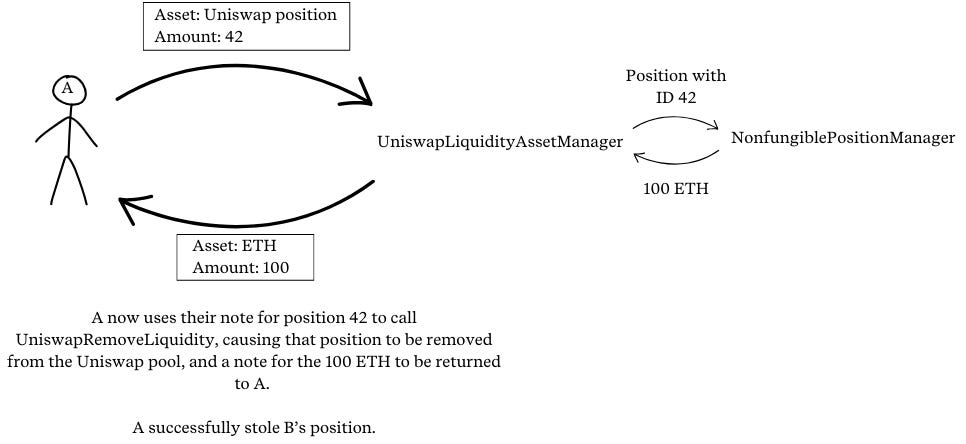
The attacker A then calls
uniswapRemoveLiquiditywith their position note with token IDb. They receive notes in return reflecting the liquidity that was originally provided by B. Should B try to remove the liquidity, they will get nothing. The attacker has thus successfully stolen B's liquidity position.
How we found the bug: Type-confusion issues of this kind are a general concern wherever data of different types is mixed. Noting that non-fungible notes were used for Uniswap positions and stored together with fungible ERC-20 notes, we checked whether any actions could be taken using non-fungible notes that should only be allowed for fungible notes, or vice-versa.
Impact of the bug: Anyone can steal Uniswap liquidity positions.
Fix for the bug: We recommended ensuring that non-fungible notes cannot be used as if they were fungible and vice-versa by domain-separating them.
Previously, fungible note commitments were given by hash(asset, amount, footer) while non-fungible note commitments were given by hash(asset, id, footer).
These could be domain-separated by using instead hash(DOMAIN_SEPARATOR_FUNGIBLE, asset, amount, footer) and hash(DOMAIN_SEPARATOR_NON_FUNGIBLE, asset, id, footer), where DOMAIN_SEPARATOR_FUNGIBLE and DOMAIN_SEPARATOR_NON_FUNGIBLE are different constants.
Proofs should then check that the new domain-separator field of notes is of the expected type. For example, the split circuit should fail for input notes that do not have DOMAIN_SEPARATOR_FUNGIBLE as the first field.
Big thanks to Singularity for their collaboration during this security assessment and for quickly fixing the issue following this recommendation.
Zellic Research & Writing
New Key-Recovery Attacks Against FHE
The security and pitfalls of fully homomorphic encryption.
In the News
Crime
Crystal Intelligence, an analytics firm, details $19B in losses due to cryptocurrency crimes in a study of the past 13 years from June 19, 2011, to March 6, 2024.
The FBI released a public service announcement warning of cybercriminals posing as law firms and lawyers that offer recovery to the victims of crypto scams.
Legal
The SEC charged Consensys for unregistered offers and sales of securities through MetaMask alleging, “that Consensys engages in the unregistered offer and sale of securities by participating in the distribution of the staking programs and operates as an unregistered broker with respect to these transactions.”
The Head of the SEC’s Crypto Assets Enforcement Division, David Hirsch, stepped down after leading the SEC’s digital asset enforcement team for nearly 10 years.
Hacks
100,000+ sites have been impacted in a supply chain attack by the service Polyfill.io after a Chinese company purchased the site and the script was modified to redirect users to malicious and scam sites.
CCN provided a full list of the major crypto hacks and scams in 2024, along with the top hacks and scams in 2023.
DeFi Hacks Analysis by SunWeb3Sec reviews 200+ DeFi security breaches by examining the underlying issues and detailed insights into the vulnerabilities exploited by the attackers.
Lykke, a UK-based crypto exchange, shut down trading two days after the exchange was hacked for $22M.
Scams
The Cybersecurity and Infrastructure Security Agency (CISA) alerted its staff of scammers claiming to be CISA employees, often using “the names and titles of government employees,” targeting crypto investors.
Deepfake scams in crypto have led to over $79B lost since early 2022 according to a report from Bitget Research.
The Ethereum Foundation disclosed that a phishing email was sent to 35,794 email addresses from updates@blog.ethereum.org which led to a website with a crypto drainer running in the background.
CoinGecko confirmed that a data breach in its third-party email management provider enabled the attacker to gain access to the contact information of its 1.9M users and send a total of 23,723 phishing emails.
Research
Apple recently introduced Private Cloud Compute, a cloud intelligence system designed specifically for private AI processing.
Professors Alessandro Chiesa and Eylon Yogev were recently on the Zero Knowledge Podcast discussing their book Building Cryptographic Proofs from Hash Functions (check out our blogs on ZK-Friendly Hash Functions and Algebraic Attacks on ZK-Friendly Hash Functions).
Comprehensive Analysis of Phishing Attacks on Blockchain by X-explore and WuBlockchain covers various types of phishing attacks and methods that can be used to prevent or identify malicious attacks in the future.
Meet Up With Us
We’ll be at the following conference in July. If you’d like to set up 1:1 time with our team, then reach out to sales@zellic.io for scheduling!
EthCC - Brussels (July 8 - 11)
Join us on the 11th from 3:00 pm - 6:00 pm at the B.Y.O.V. Mixer hosted with Superform, Morpho, and Polymer. Register here.
Recent Zellic Audit Reports
Alkimiya Audit Report: Alkimiya is a blockspace capital markets protocol that facilitates the creation, trading, and settlement of synthetic blockspace resources via a peer-to-peer system of smart contracts.
Scroll zkEVM Audit Report: Scroll seamlessly extends Ethereum’s capabilities through zero knowledge tech and EVM compatibility.
Yei Finance Oracle Audit Report: Yei Finance is a pioneering DeFi project built on Sei.
Anzen Finance Audit Report: USDz is the stablecoin created by Anzen. It is a non-rebasing, permissionless ERC20 token. USDz is always backed 1:1 by SPCT, which represents RWA as real collateral backing USDz.
Zellic Art
“Zellic Chan is thinking…”