Zellic Security Roundup: June '24
Volume 1, Issue 5
Welcome to the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month will be focused on a bug found in our recent security assessment of Silo, our recent writing which introduces one of our recently released internal Solidity tools, and the latest news in Web3 security.
Cool Finds at Zellic
What’s the finding? Calling reconcile before token distribution from unbonding led to funds stuck in the contract.
Audit: Silo Staking
Timeline: Silo’s flagship application, iSEI, offers users the ability to deposit their Sei and stake it to earn rewards while maintaining liquidity across the Defi ecosystem. During the assessment period, Zellic uncovered two findings (one high impact and one low impact). This is a look at one of the findings.
Description of the bug: Calling reconcile before token distribution from unbonding led to funds stuck in the contract. To understand how this worked, here are some key functions to know.
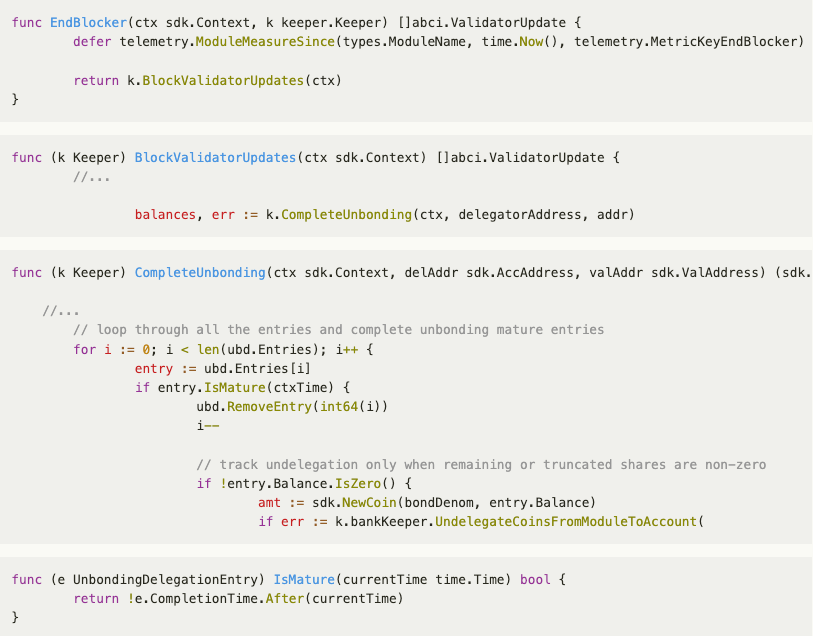
Epoch_period. Sei chains, by default, have a limit of seven undelegations at a time per validator-delegator pair. To support unbonding requests from many users, the contract bundles unbonding requests together and submits them in batches every three days. This three-day interval is defined by theepoch_periodparameter.ExecuteMsg::SubmitUnbond. At the end of the three-day period, anyone can submit the pending batch to be unbonded. Invoking theExecuteMsg::SubmitUnbondfunction would accomplish this submission. The contract calculates the amount of Sei to unbond based on the Sei/iSEI exchange rate at the time, burns the iSEI tokens, and initiates undelegations with the validators.ExecuteMsg::Reconcile. At the end of the following 21-day unbonding period, anyone can mark the batches as reconciled if the current balance of Sei is greater than what is expected or deduct the difference between the actual balance of Sei and expected Sei from the batches. Invoking theExecuteMsg::Reconcilefunction would accomplish this submission.
The tokens are also distributed in the first block after the end of the unbonding period (21 days) in the endblocker. Here is the relevant code, which transfers the tokens to the account using the call k.bankKeeper.UndelegateCoinsFromModuleToAccount:
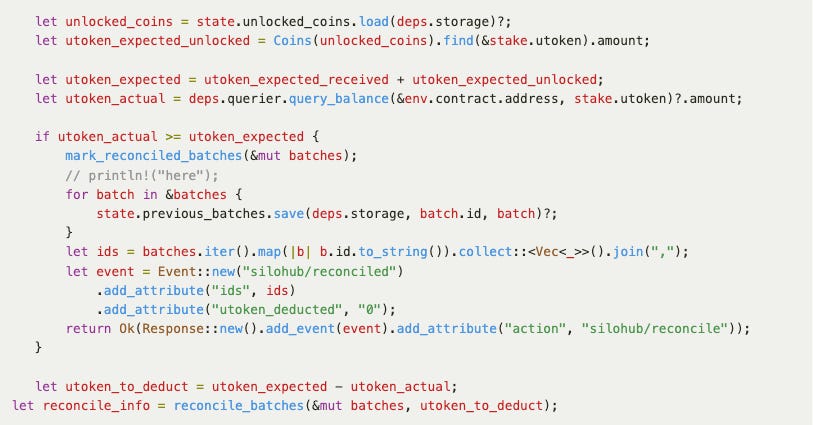
If the reconcile function is called in the same block as the token distribution, it would be executed before the token distribution and utoken_actual would be less than utoken_expected. Thus, the utoken_to_deduct amount would be deducted from the batches to be reconciled.
While there is a time check in the reconcile function, which filters out the batches with current_time > b.est_unbond_end_time to be reconciled, the token distribution could still happen in the same block due to rounding (the precision of time is seconds in CosmWasm, while it is nanoseconds in Cosmos SDK).
Assuming that a batch is submitted at epoch timestamp 1000.8, the value of est_unbond_end_time stored in the CosmWasm contract would be 1000 + 21 days (1814400) = 1815400, and reconcile could be called a second after that, which is 1815401. But as per the Go code, the exact unbonding time to distribute the tokens will be 1815400.8.
Now, let us assume two blocks, B1 at time 1815400.7 and the next block B2 at time 1815401.1 (as the approximate block time of the Sei blockchain is 0.4 seconds). At block B1, neither reconcile could be called as the value of current_time will be 1815400 and est_unbond_end_time is 1815400, nor will the token distribution happen as 1815400.7 is less than 1815400.8.
At the next block B2, the time will be 1815401.1; at this time, reconcile could be called as current_time > b.est_unbond_end_time would be true, and token distribution will happen in the endblocker. In this reconcile call, as the tokens have not been distributed yet, the contract would assume that this is due to slashing and thus deduct those Sei from the batches.
How we found the bug: While reviewing the code of the reconcile function, which is responsible for token distribution, we were interested in finding out how the CosmWasm code knows that tokens from the unbonding are returned to this contract. This led to a review of the Cosmos SDK implementation of the unbonding requests. The sole purpose of reviewing the Cosmos SDK code was to check if there is a way to call reconcile before the token transfer happens as it would lead to tokens stuck in the contract. After reviewing the Cosmos SDK implementation and writing a POC, we confirmed that it was possible to call reconcile before the token transfer, leading to a possible attack scenario.
Impact of the bug: The tokens would be stuck in the contract, and users would not be able to withdraw them unless the contract is migrated and the admin rescues these tokens and distributes them to the users.
Fix for the bug: We recommended a fix of adding a few seconds of delay in the reconcile call so it could not be called in the same block as the token distribution. This fix was quickly implemented by the Silo team.
Zellic Research & Writing
SOLP: A Stand-alone Solidity Analysis Library
Zellic is proud to announce SOLP, a library for analyzing and transforming Solidity source code.
Zellic Elected to Arbitrum’s Security Council
Zellic will help govern the Arbitrum ecosystem and protocol risk, we look forward to continuing our service of the Arbitrum community, along with our work with the ecosystem's most innovative, including Premia, Y2K, and Perennial.
In the News
Crime
Alexey Pertsev, the Tornado Cash developer, was recently sentenced to 64 months in jail on charges of money laundering by a Dutch Court.
The U.S. Department of Justice identified the leader of the LockBit Ransomware gang and is offering a reward of $10M for information that leads to his arrest.
Brothers arrested and charged with conspiracy to commit wire fraud, wire fraud, and conspiracy to commit money laundering for stealing $25M in ETH.
Former FTX Digital Markets co-CEO Ryan Salame was sentenced to 7.5 years in prison after pleading guilty to conspiracy to operate an unlicensed money transmitting business and engaging in campaign finance fraud.
Hacks
$181,000 was stolen from the defunct DeFi protocol, Yield Protocol, despite multiple warnings from the protocol advising investors to close their positions.
More than 70% of funds stolen by the Lazarus Group were stolen via private key exploits according to CoinTelegraph Magazine’s analysis of data from the United Nations Security Council (UNSC) and DeFiLlama.
Rain, a Bahrain-based crypto exchange, was exploited for $14.8M which was divided into wallets containing 137.9 BTC and 1,881 ETH.
The hacker of Poloniex, a crypto exchange, moved 17,800 ETH from six different wallets through Tornado Cash.
Gala Games was hacked for ~$206M in $GALA, the exploit occurred through an admin address.
Sonne Finance, a decentralized lending protocol, was exploited for ~$20M due to a vulnerability in Compound v2 forks.
Scams
The wallet-draining service Pink Drainer announced the end of its services for its customers who have used it to steal more than $75 million over the past year.
A trader lost $68M of Wrapped Bitcoin in an address-poisoning scam leaving them with just $13.56 worth of ETH.
A group of major tech companies, including Meta, Coinbase, Match Group, and others, jointly launched a new coalition to take on online fraud across crypto.
Research
The SSID Confusion Attack is a vulnerability that exploits a design flaw in the WiFi standard, allowing attackers to trick WiFi clients on any operating system into connecting to an untrusted network.
Meet Up With Us
We’ll be at the following conference in May. If you’d like to set up 1:1 time with our team, then reach out to sales@zellic.io for scheduling!
EthCC - Brussels (July 8 - 11)
Recent Zellic Audit Reports
Adrastia PID Controller Audit Report: Adrastia’s PID controller system automatically optimizes the output to minimize the input error.
Trillion Audit Report: Trillion is a new stablecoin provider issuing fiat-backed, fully reserved centralized stablecoins.
WOOFi Audit Report: WOOFi is a decentralized exchange that bridges the deep liquidity of centralized exchanges on chain.
Omron Audit Report: Omron provides verified inferences of restaking optimizations to improve efficiency and yields in existing liquid restaking protocols.