Zellic Security Roundup: May '25
Volume 2, Issue 5
Welcome to the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month we will dive into two vulnerabilities discovered in TON by Zellic Security Researcher Nan Wang, recently published Zellic blogs and threads, and the latest news in Web3 security.
Cool Finds at Zellic
The following is a summary of the vulnerabilities discovered in TON. These are not issues with contracts developed on top of TON but in the blockchain itself.
These vulnerabilities were discovered by Zellic Security Researcher Nan Wang.
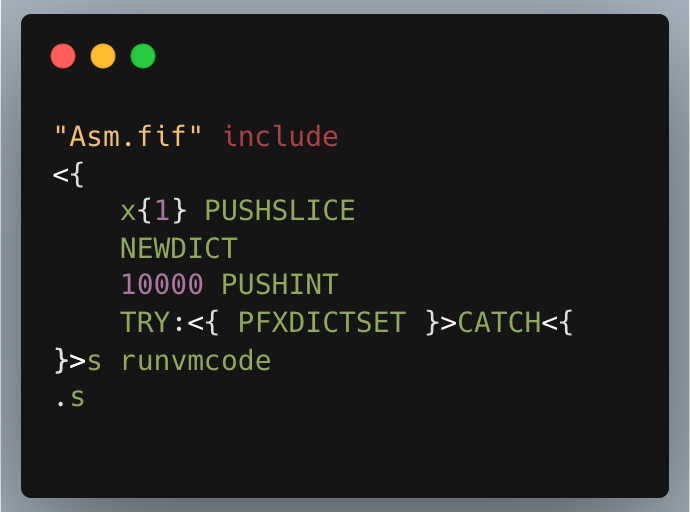
Inaccurate PFXDICT Instruction Parameters Validation
Impact of this vulnerability: PFXDICT instruction parameter validation insufficiency leads to serious security risks. The TVM only checks for 3 parameters instead of the required 4, violating the exception-handling mechanism specified in the virtual machine documentation. This causes stack operation errors to be masked as range check errors.
Attackers can exploit this discrepancy to construct specific inputs, bypassing security checks to enter abnormal execution paths. In smart contracts handling large amounts of funds, such low-level execution differences may evolve into major financial risks, damaging platform credibility.
The following code snippet contains a vulnerability. The relevant code can be found here.
PFXDICT operations are expected to have stack parameters in the form of x k D n as defined in the TVM instruction documentation. However, the stack.check_underflow(3) validation simply checks for the presence of three parameters. This means that, in cases where the stack is empty, the `pop_cellslice` function can potentially trigger a denial of service.
While internal checks in the pop_cellslice function mitigates some denial-of-service risks, it still opens up potential correctness issues.
Here's the proof-of-concept code illustrating this problem:
This has an incorrect parameter count. Thus, according to the TON Virtual Machine documentation, one would expect to throw the handling exception code 2: stack underflow error. However, in reality, the parameter check is circumvented, leading to a handling exception code 5: integer out of range error instead.
You can find TON's response to this vulnerability in this commit.
Out-of-Bounds–Read Vulnerability Due to Inadequate UTF Encoding String Management
Impact of this vulnerability: Logical flaws in the get_utf8_from_utf16_length function may lead to out-of-bounds reads of array p. When processing UTF-16 strings containing high surrogate code units (0xD800–0xDBFF), under certain conditions the index i may be prematurely incremented, causing out-of-bounds memory access and potentially triggering program crashes. This code section was previously used in an unsupported legacy Android wallet, therefore the actual impact is minimal.
This vulnerability occurs within a segment of the tl_parser code. The relevant code can be viewed here.
The function get_utf8_from_utf16_length(const jchar *p, jsize len), which contains the above logic, incorporates an out-of-bounds-read vulnerability for the p array. This function is designed to calculate the required UTF-8 byte length for a UTF-16 string.
However, under certain conditions that include high-surrogate code units (0xD800–0xDBFF), the loop prematurely increments the index variable i. This results in referencing an element that exceeds the array boundaries, ultimately causing out-of-bounds memory access.
You can find TON's response to this vulnerability in this commit.
Zellic Research & Writing
TON Security Primer: Part 1
A look into The Open Network, its unique design choices, and the security considerations for building on TON.
Choosing an Audit Competition: How to Spot Snake Oil
A review of common misleading sales tactics used for audit competitions and the questions you should ask.
Building with Bitcoin: A Survey of the Use of Its Scripting System Across Projects
A look into Bitcoin's scripting system and how several projects use Bitcoin's features in their own software.
In the News
Hacks
An elderly US citizen was the victim of a $330M Bitcoin theft where the attacker used social-engineering techniques to gain access to the victim’s wallet. The stolen funds were laundered through six exchanges and swapped into Monero. This incident ranks as the fifth-largest crypto hack in history.
The swap into Monero led to a 38% price jump in Monero’s XMR token.
Security research firm Oligo discovered a set of vulnerabilities in Apple’s AirPlay protocol and the AirPlay SDK that allows attackers to, amongst many other vectors and outcomes, weaponize wormable zero-click RCE exploits.
A bug was identified in Kelp after excess rsETH ($31,220,047,901,664,100,000) was minted to the Kelp Treasury as a protocol fee. The code used a 1e36 base, rather than the typical 1e18 base, which made what looked like a correct fee calculation result in a number that is 1,000,000,000,000,000,000x too big (write-up by @danielvf).
The hacker behind the $5.8M Loopscale exploit has indicated a willingness to negotiate the return of the stolen funds in exchange for a bounty. Loopscale’s team offered the hacker a 10% bounty and a full release of liability in exchange for a 90% return of the stolen funds.
A hacker infected a key piece of developer software for the XRP Ledger blockchain, software that is used by “hundreds of thousands of applications and websites making it a potentially catastrophic supply chain attack on the cryptocurrency ecosystem”, according to Aikido security researcher Charlie Eriksen.
Research
The Cybersecurity and Infrastructure Security Agency signed an 11-month contract extension to help avoid the shutdown of the Common Vulnerabilities and Exposures (CVE) and Common Weakness Enumeration (CWE) programs.
Zellic published a thread on Babylon, the proof-of-stake blockchain where Bitcoin is the staked asset, which reviews the high-level design of Babylon along with how a few of Bitcoin’s key features are used in its software.
Zellic published a thread on how to spot misleading audit competition metrics and what to watch out for when evaluating an audit competition platform.
Slopsquatting, a new class of supply-chain attacks, has emerged from the increased use of generative AI tools for coding and the model's tendency to hallucinate nonexistent package names.
Scams
Threat actors linked to North Korea have set up front companies as a way to distribute malware during fake hiring processes. According to Silent Push, “the threat actor group is using three front companies in the cryptocurrency consulting industry – BlockNovas LLC (blocknovas[.] com), Angeloper Agency (angeloper[.]com), and SoftGlide LLC (softglide[.]co)”.
The FBI’s Internet Crime Complaint Center (IC3) has released its annual report detailing complaints and losses due to scams/fraud involving cryptocurrency. The 2024 report received 140,000+ complaints, which totaled ~$9.3B in losses.
The report also found that individuals 60 years and older lost $2.8B, the age range that reported the highest total losses.
nick.eth, lead developer of ENS, was targeted by a phishing attack that exploited a vulnerability in Google’s infrastructure that would lead to credential harvesting. The phishing attack was sent from a valid, signed email and directed the user to a legacy website using the google.com domain.
Legal
The UK’s Treasury and Chancellor of the Exchequer Rachel Reeves has announced draft rules for cryptocurrencies that would bring “crypto exchanges, dealers and agents” in line with regulations, as many residents were “exposed to risky firms and scams”.
Crime
Prodaft, a Swiss cybersecurity firm, launched the Sell Your Source initiative where the company purchases verified and aged accounts on hacking forums to spy on cybercriminals. The goal of this program is to use these accounts to infiltrate these communities to collect intelligence that could expose malicious operations and platforms.
Andean Medjedovic, a Canadian math prodigy, is facing five criminal charges including wire fraud, attempted extortion, and money laundering after stealing more than $60M in cryptocurrency according to a US federal court document.
Meet Up With Us
We’ll be at these following conferences in May, if you’d like to set up 1:1 time with our team, then reach out to sales@zellic.io for scheduling!
Consensus 2025 (Toronto): May 14–16
Solana Accelerate (NYC): May 19–24
Zellic Auditing Stats
In April, Zellic auditors completed 24 audit engagements where they were able to uncover a total of 56 Critical, High, and Medium bugs:
7 Critical-level bugs
6 Coding Mistakes bugs
1 Business Logic bug
23 High-level bugs
19 Coding Mistakes bugs
2 Business Logic bugs
2 Protocol Risk bugs
26 Medium-level bugs
20 Coding Mistakes bugs
5 Business Logic bugs
1 Protocol Risk bug
Recent Zellic Audit Reports
StakeKit Audit Report: StakeKit is a self-custodial staking and DeFi API that enables wallets, custodians, and dApps to integrate staking.
Radix Audit Report: Radix is a layer-1 smart contract protocol built for DeFi, providing a radically better user and developer experience.
Cetus Protocol Audit Report: Cetus is a leading decentralized exchange, which serves as the key liquidity and swap infra of the Sui ecosystem.
About Us
Zellic specializes in securing emerging technologies. Our security researchers have uncovered vulnerabilities in the most valuable targets, from Fortune 500s to DeFi giants.
Developers, founders, and investors trust our security assessments to ship quickly, confidently, and without critical vulnerabilities. With our background in real-world offensive security research, we find what others miss.
Contact us for real audits, not rubber stamps.