Zellic Security Roundup: November '24
Volume 1, Issue 10
Welcome to the Zellic Security Roundup, a monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month will focus on Masamune, the smart contract security search tool designed for smart contract developers and security researchers, along with our recently completed audit reports and the latest news in Web3 security.
Cool Finds at Zellic
What Is Masamune?
Masamune is a utility that allows searching for smart contract security insights. It can identify potential pitfalls from a curated list of audit reports, bug fixes, and technical documentation of various protocols. It makes extracting insights easy for all, regardless of security expertise.
Currently, two versions of Masamune are available: V1 and V2. Their differences are listed below:
V1 relies on plain regex rules, which match the keyword you input against the entire collection of data sources. The advantage of this approach is precision. You’re getting all the results that contain the specific keyword you queried.
V2 is a regex search enhanced by AI and is still under development. All the data sources are embedded using OpenAI’s embedding↗. It then handles the embeddings via FAISS↗, an open-source library for efficient similarity search. The advantage of this approach is contextual understanding and broader relevance — V2 can interpret the meaning behind your query, providing results that are contextually related, while capturing nuances that plain regex searches would miss.
How Does Masamune Work?
Masamune is designed with simplicity in mind, following the Pareto (80-20) rule↗. This principle suggests that 80% of the results come from 20% of the effort. In the case of Masamune, it means that the tool is optimized to provide the most valuable results with minimal querying effort. This makes it highly effective for modeling the initial stages of the problem you’re trying to solve.
For example, let’s imagine we are developing a protocol that integrates with Uniswap. Using V1, our query would simply be “uniswap”.
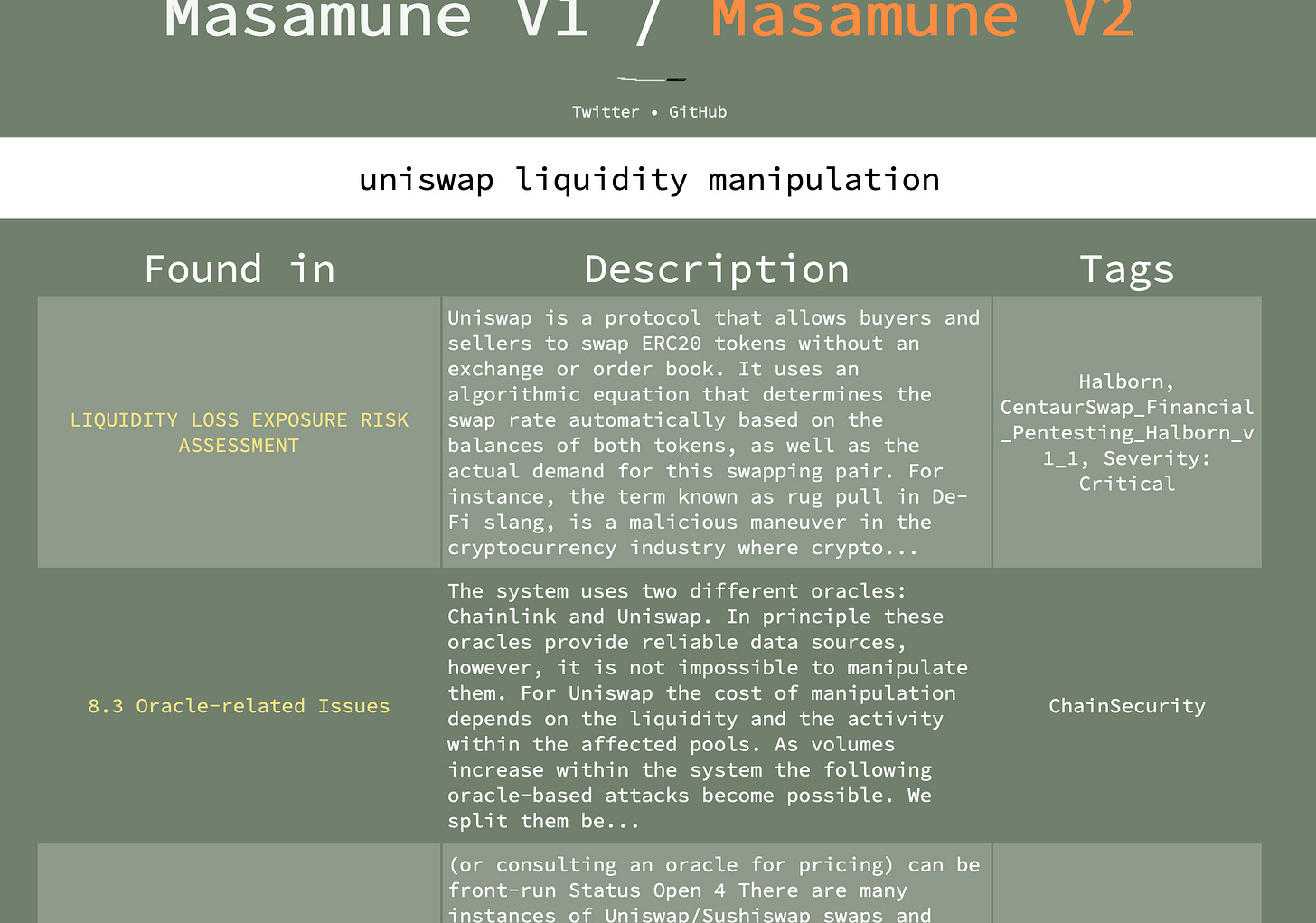
Masamune then lists all the results that match “uniswap”, either based on their title or the body text. These results require further details, as our search targeted a broad topic. Let’s say we want to access the second result, “UniswapConfig getters return wrong token config if token config does not exist”. In this particular case, we’re dealing with a finding identified during a Code4rena contest, hence the GitHub issue format. By clicking on the hyperlink↗, we can view all the details of the finding.
This information helps us understand what went wrong, what the impact of the vulnerability was, and how to mitigate it, to avoid repeating any similar mistakes.
While a more specific query might provide more accuracy, the regex-based approach in V1 offers a straightforward and efficient way to gather initial data. This simplicity is advantageous in the early stages of development, as it allows for quick identification of generally relevant information.
As a project matures, its complexity inevitably increases. This growing complexity demands not just any quick insights but context-aware and highly specific ones. The deeper and more intricate the codebase becomes, the more nuanced the queries must be to effectively address the emerging challenges.
To address this need for nuanced queries and more sophisticated insights, we developed V2.
For smart contract developers, staying up-to-date with the latest security issues and bug fixes is a constant struggle, and it’s hard to know what you don’t know. To ease this learning curve, V2 allows for a more context-aware search using OpenAI embeddings, which widen the results’ breadth. This way, even if you can’t leverage the precision of V1, the additional flexibility of V2 attracts results that would have previously been missed by the same query.
Zellic Research & Writing
Masamune: The Smart Contract Security Search Tool
Zellic is proud to announce Masamune, a curated index of audit reports, bug fixes, and technical documentation of numerous protocols.
In the News
Research
“Why Code Security Matters - Even in Hardened Environments” is a presentation turned blog post by Stefan Schiller, which highlights the importance of fundamental code security “by showcasing a technique that attackers can use to turn a file write vulnerability in a Node.js application into remote code execution”.
Visa introduced its new Visa Tokenized Asset Platform (VTAP), which is a
”new product designed to help financial institutions issue and manage fiat-backed tokens on blockchain network”.Ethereum remains the top blockchain for whitehat hackers, followed by Polygon, Arbitrum, and Solana according to a recent Immunefi report.
Zellic Co-Founder and CEO Luna Tong joined CoinFund CEO Jake Brukhman on the Mined with CoinFund Podcast, discussing AI's role in security audits, the pre-mainnet auditing process, and Web2 versus Web3 cybersecurity.
Legal
The U.S. Department of Justice has filed two forfeiture actions in an attempt to seize ~$2.67M worth of cryptocurrency stolen in the hack of Deribit by the North Korean–linked Lazarus Group and in the hack of Stake.com.
A Nigerian Court ordered the release of Binance Executive Tigran Gambaryan after Nigeria’s Economic and Financial Crimes Commission (EFCC) withdrew the case of money-laundering charges against him. The EFCC said it would continue the money-laundering case against Binance without Gambaryan.
Crime
Eighteen individuals and entities have been charged with fraud and manipulation in the cryptocurrency market. More than $25M in cryptocurrency has been seized, and multiple trading bots have been deactivated.
The FBI arrested a man involved in the unauthorized takeover of the US Securities and Exchange Commission’s Twitter account. The individual posted a fake message from the SEC Chair, which caused the value of Bitcoin to increase by $1,000.
Unit 42 has tracked activity from threat actors associated with the Democratic People’s Republic of Korea posing as recruiters to install malware on job seekers’ devices with two recent code updates found in the BeaverTail downloader and InvisibleFerret backdoor.
Hacks
Radiant Capital suffered a hack that led to the loss of over $50M, which marks the second significant exploit that the protocol has faced in 2024. The hacker has moved the stolen funds from the exploit from Arbitrum and Binance BNB Chain to Ethereum.
A US government—controlled wallet containing funds from the 2016 Bitfinex hack was drained of $20M, but most of the funds were returned less than 24 hours after the initial address breach.
CCN has updated its ongoing list of crypto hacks in 2024 to reflect the recent hacks that took place in October.
A Chinese OTC trader has been accused of helping the Lazarus Group cash out money stolen from multiple hacks. A ZachXBT investigation revealed the trader’s connection to numerous transactions tied to a hack performed by the Lazarus Group.
Security analysts from Kaspersky Labs discovered that the Lazarus Group executed an attack that used a fake NFT-based game to exploit a zero-day vulnerability in Google Chrome. This vulnerability allowed the attackers to access the crypto wallets of its victims.
Scams
Authorities in Thailand have dismantled a cross-border fraud group conducting identity theft, fraudulent investments, and money laundering after a local woman was scammed for $621,000 through crypto investments.
The FBI arrested two men from Florida and California for their alleged involvement in a $230M cryptocurrency scam where they defrauded a victim of over 4,100 Bitcoin.
Deepfake scams in the crypto sector saw a 654% growth from 2023 to 2024 with 74% of all deepfake scam attempts happening in the crypto industry.
Meet Up With Us
We will be traveling to the following conferences in November. If you’d like to schedule 1:1 time with our team, reach out to sales@zellic.io:
Devcon 2024 — Bangkok (November 12-15)
Recent Zellic Audit Reports
MetaLeX Metavest Audit Report: MetaVesT is a BORG-compatible token-vesting/lockup protocol for ERC-20 tokens.
Grug Audit Report: Grug is an execution environment for blockchains. The scope of this audit was the state commitment scheme that Grug uses, the Jellyfish Merkle Tree.
Omni Network Audit Report: Omni combines an EVM execution layer with native cross-chain messaging, both secured by Omni’s consensus-layer DPOS validator set.
Session Token Audit Report: Session is an end-to-end encrypted, decentralized messaging application.