Zellic Security Roundup: September '25
Volume 2, Issue 9
Welcome to the September edition of the Zellic Security Roundup, the monthly security-focused newsletter covering valuable security news and analysis in Web3.
This month, we will look at our latest blog that covers WebViews and the common security pitfalls for mobile developers, the recent security news in Web3, and our latest audit reports.
Zellic Research & Writing
Below is a snippet from our blog post “You’re Probably Using WebViews Wrong: Common Security Pitfalls for Mobile Developers” written by Zellic Security Researcher Bryce.
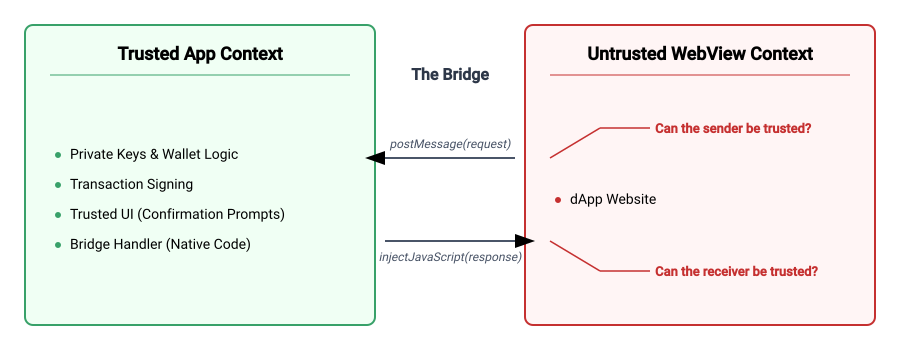
When a dApp calls one of our APIs, it should send some data or message to us that we can handle. But where do we handle this data?
It would be bad if we processed sensitive user data inside of the WebView, since the webpage (which is potentially untrusted) could read and tamper with our user’s data. Instead, we need to process this data outside of the WebView, and we can create a bidirectional communication bridge between the two. This allows us to keep all the sensitive data inside of our app.
The react-native-webview library allows us to implement this using postMessage. The webpage can send messages to our app, and our app can process them and send a response back to the page.
This communication bridge is an essential part of our threat model, as it connects our trusted app to the untrusted, potentially malicious webpage.
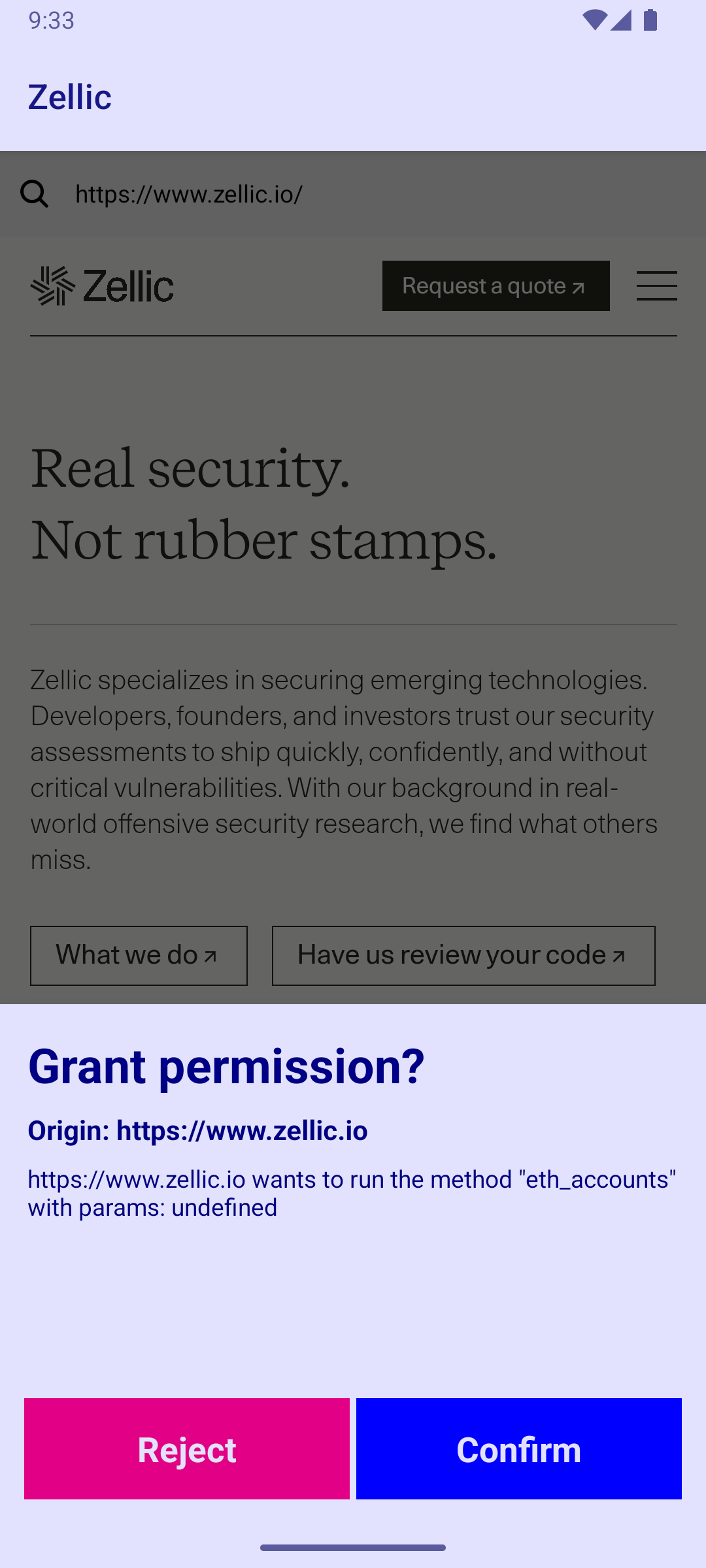
However, a complete threat model must also consider the user interface (UI). Securing the bridge is pointless if the user can be tricked into authorizing malicious requests. Therefore, the second critical part of our threat model is maintaining a clear separation between trusted and untrusted UI elements.
In a standard mobile browser, the address bar is a trusted UI element; it’s the user’s primary indicator of the website’s URL. The webpage itself only controls the pixels below this address bar, in the untrusted content area. If a malicious website could somehow draw over the address bar, it could spoof its URL and deceive the user.
This distinction between trusted and untrusted UI becomes even more critical in a wallet app. When a dApp requests a signature, the wallet must display a confirmation prompt. This prompt is a trusted UI element, displaying critical security information like the origin of the request and the action being performed. The user assumes everything in this prompt is trustworthy.
Any failure to correctly model and defend these two attack surfaces — the communication bridge and the trusted UI — can jeopardize the security of the wallet and put user funds at risk. Unfortunately, getting this right is very difficult.
Here are some key takeaways for developers working on crypto wallet apps:
Separate trusted and untrusted UI clearly. Establish clear visual boundaries between content controlled by your app versus untrusted content displayed from webpages. While the WebView API is provided to you, you are essentially rebuilding the browser UI from scratch.
Consider the entire bridge attack surface. Your bridge is a two-way street. Remember both request sending and response receiving can be compromised, and design your implementation with this in mind.
Test extensively across platforms. There are differences between iOS and Android WebView APIs that can create subtle but exploitable vulnerabilities.
Assume compromise. Consider adding additional defense in depth countermeasures in the case that malicious content reaches your bridge — for example, transaction simulation, integrating with platforms that can detect potentially malicious transactions, and so on.
The principles and techniques discussed here don’t just apply to crypto wallets but to any application that embeds web content while handling sensitive operations. As the mobile ecosystem continues to evolve and WebViews become increasingly prevalent, understanding and mitigating these attack vectors will only become more important.
In the News
Hacks
Following the largest supply-chain attack in the history of the NPM ecosystem, which impacted around 10% of all cloud environments, the attackers only stole ~$20.
Twelve DeFi protocols, with a combined $20B in deposits, have adopted the Security Alliance’s Safe Harbor Agreement, an on-chain legal agreement that protocols can adopt so that security researchers can rescue a protocol during an ongoing attack.
ReversingLabs identified two open-source packages that use Ethereum smart contracts to download malware as part of a bigger campaign of malicious actors attempting to hack users via poisoned blockchain-related public code libraries.
Venus Protocol stakeholders voted to pass an action plan to liquidate an attacker just hours after the hacker stole $13.5M from a Venus Protocol user.
Research
Code4rena recently launched an audit competition for Monad with the largest-ever unconditional prize pool of $500,000. The competition runs until October 12th.
Rich Widmann, the Head of Strategy of Web3 at Google, shares a comparative chart between the Stripe, Circle, and Google Cloud L1 blockchains.
The Ethereum Foundation (EF) announced Phase 2 of their Trillion Dollar Security project, which includes “acting on the highest priority issues we face”. EF will first focus on UX issues, as their “research showed these to be the most urgent issues facing both individual and institutional users of Ethereum and Ethereum-based applications”.
Security researcher Marektoth shared their research on DOM-based extension clickjacking. In their research, which was originally presented at DEF CON 33, Marektoth describes “a new attack technique with multiple attack variants and tested it against 11 password managers. This resulted in discovering several 0-day vulnerabilities that could affect the stored data of tens of millions of users”.
Scams
According to Deputy Assistant Director Michael Machtinger in the FBI’s cyber division, in reference to China’s Salt Typhoon cyberspies, “there's a good chance this espionage campaign has stolen information from nearly every American”.
Security researchers have uncovered a new campaign that leverages ConnectWise ScreenConnect, a remote monitoring and management software, to deliver a fleshless loader that drops a remote access trojan to steal sensitive data.
ModStealer, a newly discovered malware, is targeting crypto users to steal private keys, certificates, credential files, and browser-based wallet extensions.
Legal
The Department of the Treasury’s Office of Foreign Assets Control has redesignated the crypto exchange Garantex. Garantex has directly facilitated notorious ransomware actors and other cybercriminals by processing over $100M in transactions linked to illicit activities since 2019.
Coinbase has filed a legal motion requesting a hearing and potential remedies after the SEC failed to comply with the Freedom of Information Act filings from 2023 and 2024.
Crime
African authorities have arrested 1,209 cybercriminals in a crackdown that has recovered $97.4M and dismantled 11,432 malicious infrastructures.
Blockscope released its mid-year 2025 crypto crime report, which looks at the state of crypto crime in H1 2025 compared to H1 2024, key trends, crypto crime tactics, and more.
A Canadian teen behind a $35M crypto heist using a SIM swap is now serving a one-year sentence in the US and owes $600K+ in fines and restitution.
The US Department of Justice seized over $5M in Bitcoin, which was stolen through SIM-swapping attacks from October 2022 to March 2023.
Meet Up With Us
We’ll be attending the following conferences in September and October. If you’d like to schedule a one-on-one meeting with our team, please reach out to sales@zellic.io for scheduling.
Korea Blockchain Week: September 22 – 28
TOKEN2049: October 1 – October 2
Zellic Auditing Stats
In August, Zellic auditors completed 19 audit engagements where they were able to uncover a total of 100 Critical, High, and Medium bugs:
33 Critical-level bugs
31 Coding Mistakes bugs
2 Business Logic bugs
37 High-level bugs
30 Coding Mistakes bugs
7 Business Logic bugs
30 Medium-level bugs
20 Coding Mistakes bugs
10 Business Logic bugs
Recent Zellic Audit Reports
Mitosis Extensible Vaults Audit Report: Mitosis is an L1 network designed for programmable liquidity that enhances the liquidity-provision experience for both DeFi projects and liquidity providers.
Aori 0.3.1 Upgrade Audit Report: Aori is designed to securely facilitate performant trade execution with trust-minimized settlement from any chain to any chain.
Odos Cross-Chain Audit Report: Odos Cross-Chain provides a suite of smart contracts designed to facilitate seamless interaction between Odos and the Across Protocol.
Frax Audit Report: Frax Finance is building scalable stablecoin infrastructure for the next generation of finance.
About Us
Zellic specializes in securing emerging technologies. Our security researchers have uncovered vulnerabilities in the most valuable targets, from Fortune 500s to DeFi giants.
Developers, founders, and investors trust our security assessments to ship quickly, confidently, and without critical vulnerabilities. With our background in real-world offensive security research, we find what others miss.
Contact us for real audits, not rubber stamps.